INCIBE
Botnets are one of the online threats with the biggest presence, causing billionaire losses to global economies. Nowadays, the increasing number of devices connected to the Internet makes it necessary to analyze large amounts of network traffic data. In this work, we focus on increasing the performance on botnet traffic classification by selecting those features that further increase the detection rate. For this purpose we use two feature selection techniques, Information Gain and Gini Importance, which led to three pre-selected subsets of five, six and seven features. Then, we evaluate the three feature subsets along with three models, Decision Tree, Random Forest and k-Nearest Neighbors. To test the performance of the three feature vectors and the three models we generate two datasets based on the CTU-13 dataset, namely QB-CTU13 and EQB-CTU13. We measure the performance as the macro averaged F1 score over the computational time required to classify a sample. The results show that the highest performance is achieved by Decision Trees using a five feature set which obtained a mean F1 score of 85% classifying each sample in an average time of 0.78 microseconds.
The unevenness importance of criminal activities in the onion domains of the
Tor Darknet and the different levels of their appeal to the end-user make them
tangled to measure their influence. To this end, this paper presents a novel
content-based ranking framework to detect the most influential onion domains.
Our approach comprises a modeling unit that represents an onion domain using
forty features extracted from five different resources: user-visible text, HTML
markup, Named Entities, network topology, and visual content. And also, a
ranking unit that, using the Learning-to-Rank (LtR) approach, automatically
learns a ranking function by integrating the previously obtained features.
Using a case-study based on drugs-related onion domains, we obtained the
following results. (1) Among the explored LtR schemes, the listwise approach
outperforms the benchmarked methods with an NDCG of 0.95 for the top-10 ranked
domains. (2) We proved quantitatively that our framework surpasses the
link-based ranking techniques. Also, (3) with the selected feature, we observed
that the textual content, composed by text, NER, and HTML features, is the most
balanced approach, in terms of efficiency and score obtained. The proposed
framework might support Law Enforcement Agencies in detecting the most
influential domains related to possible suspicious activities.
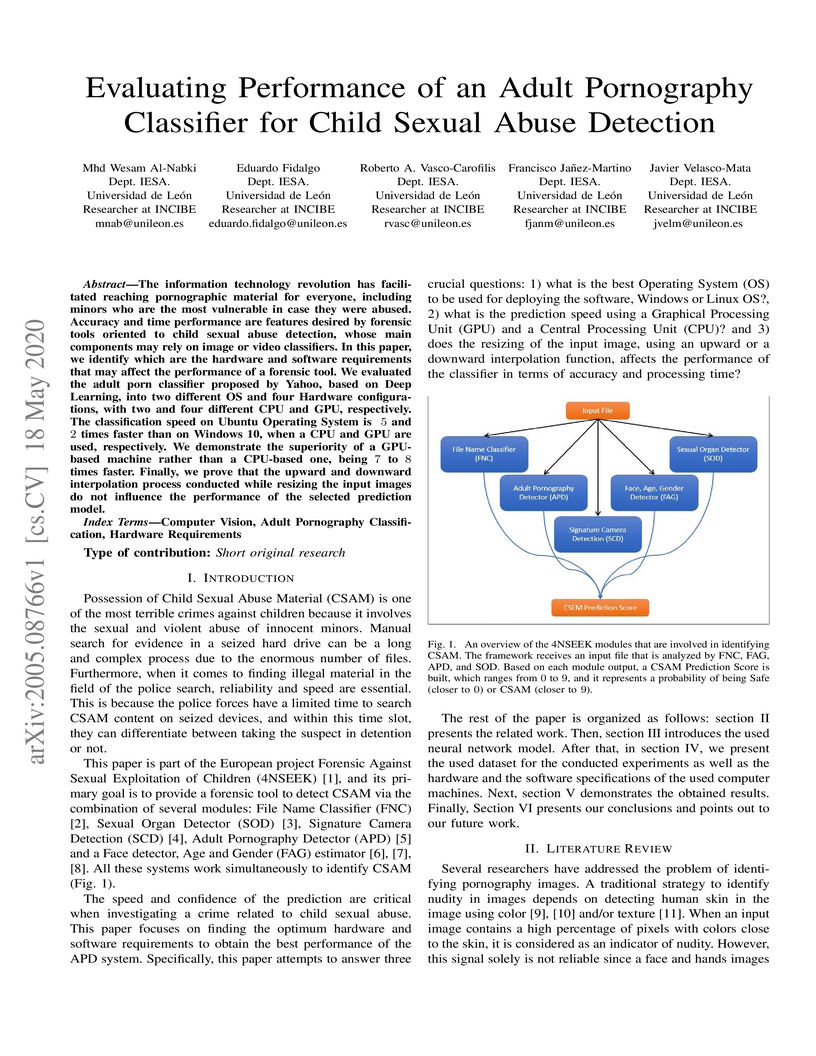
The information technology revolution has facilitated reaching pornographic material for everyone, including minors who are the most vulnerable in case they were abused. Accuracy and time performance are features desired by forensic tools oriented to child sexual abuse detection, whose main components may rely on image or video classifiers. In this paper, we identify which are the hardware and software requirements that may affect the performance of a forensic tool. We evaluated the adult porn classifier proposed by Yahoo, based on Deep Learning, into two different OS and four Hardware configurations, with two and four different CPU and GPU, respectively. The classification speed on Ubuntu Operating System is 5 and 2 times faster than on Windows 10, when a CPU and GPU are used, respectively. We demonstrate the superiority of a GPU-based machine rather than a CPU-based one, being 7 to 8 times faster. Finally, we prove that the upward and downward interpolation process conducted while resizing the input images do not influence the performance of the selected prediction model.
There are no more papers matching your filters at the moment.