UNSW Canberra
Traditional Human-Swarm Interaction (HSI) methods often lack intuitive real-time adaptive interfaces, making decision making slower and increasing cognitive load while limiting command flexibility. To solve this, we present SwarmChat, a context-aware, multimodal interaction system powered by Large Language Models (LLMs). SwarmChat enables users to issue natural language commands to robotic swarms using multiple modalities, such as text, voice, or teleoperation. The system integrates four LLM-based modules: Context Generator, Intent Recognition, Task Planner, and Modality Selector. These modules collaboratively generate context from keywords, detect user intent, adapt commands based on real-time robot state, and suggest optimal communication modalities. Its three-layer architecture offers a dynamic interface with both fixed and customizable command options, supporting flexible control while optimizing cognitive effort. The preliminary evaluation also shows that the SwarmChat's LLM modules provide accurate context interpretation, relevant intent recognition, and effective command delivery, achieving high user satisfaction.
Personal autonomous vehicles are cars, trucks and bikes capable of sensing
their surrounding environment, planning their route, and driving with little or
no involvement of human drivers. Despite the impressive technological
achievements made by the industry in recent times and the hopeful announcements
made by leading entrepreneurs, to date no personal vehicle is approved for road
circulation in a 'fully' or 'semi' autonomous mode (autonomy levels 4 and 5)
and it is still unclear when such vehicles will eventually be mature enough to
receive this kind of approval. The present review adopts an integrative and
multidisciplinary approach to investigate the major challenges faced by the
automative sector, with the aim to identify the problems that still trouble and
delay the commercialization of autonomous vehicles. The review examines the
limitations and risks associated with current technologies and the most
promising solutions devised by the researchers. This negative assessment
methodology is not motivated by pessimism, but by the aspiration to raise
critical awareness about the technology's state-of-the-art, the industry's
quality standards, and the society's demands and expectations. While the survey
primarily focuses on the applications of artificial intelligence for perception
and navigation, it also aims to offer an enlarged picture that links the purely
technological aspects with the relevant human-centric aspects, including,
cultural attitudes, conceptual assumptions, and normative (ethico-legal)
frameworks. Examining the broader context serves to highlight problems that
have a cross-disciplinary scope and identify solutions that may benefit from a
holistic consideration.
09 Apr 2001
We discuss the Aromatic Infrared Band (AIB) profiles observed by ISO-SWS towards a number of bright interstellar regions where dense molecular gas is illuminated by stellar radiation. Our sample spans a broad range of excitation conditions (exciting radiation fields with effective temperature, Teff, ranging from 23,000 to 45,000 K). The SWS spectra are decomposed coherently in our sample into Lorentz profiles and a broadband continuum. We find that the individual profiles of the main AIBs at 3.3, 6.2, 8.6 and 11.3 microns are well represented with at most two lorentzians. Furthermore, we show that the positions and widths of these AIBs are remarkably stable (within a few cm-1). We then extract the profiles of individual AIBs from the data and compare them to a model of Polycyclic Aromatic Hydrocarbon (PAH) cation emission which includes the temperature dependence of the AIB profiles. The present similarity of the AIB profiles requires that the PAH temperature distribution remains roughly the same whatever the radiation field hardness. Deriving the temperature distribution of interstellar PAHs, we show that its hot tail, which controls the AIB spectrum, sensitively depends on Nmin (the number of C-atoms in the smallest PAH) and Teff. Comparing the observed profiles of the individual AIBs to our model results, we can match most of the AIB profiles if Nmin is increased with Teff. We then discuss our results in the broader context of ISO observations of fainter interstellar regions where PAHs are expected to be in neutral form.
Polycyclic aromatic hydrocarbons (PAHs) are ubiquitous in astrophysical environments, as revealed by their pronounced emission features at 3.3, 6.2, 7.7, 8.6, 11.3, and 12.7 μm commonly ascribed to the C--H and C--C vibrational modes. Although these features have long been predicted to be polarized, previous searches for PAH polarization led to null or, at best, tentative detections. Here we report the definite detection of polarized PAH emission at 11.3 μm in the nebula associated with the Herbig Be star MWC 1080. We measure a polarization degree of 1.9±0.2\%, which is unexpectedly high compared to models. This poses a challenge in the current understanding of the alignment of PAHs, which is required to polarize the PAH emission but thought to be substantially suppressed. PAH alignment with a magnetic field via a resonance paramagnetic relaxation process may account for such a high level of polarization.
In this paper, we develop an online optimization algorithm for solving a class of nonconvex optimization problems with a linearly varying optimal point. The global convergence of the algorithm is guaranteed using the circle criterion for the class of functions whose gradient is bounded within a sector. Also, we show that the corresponding Luré-type nonlinear system involves a double integrator, which demonstrates its ability to track a linearly varying optimal point with zero steady-state error. The algorithm is applied to solving a time-of-arrival based localization problem with constant velocity and the results show that the algorithm is able to estimate the source location with zero steady-state error.
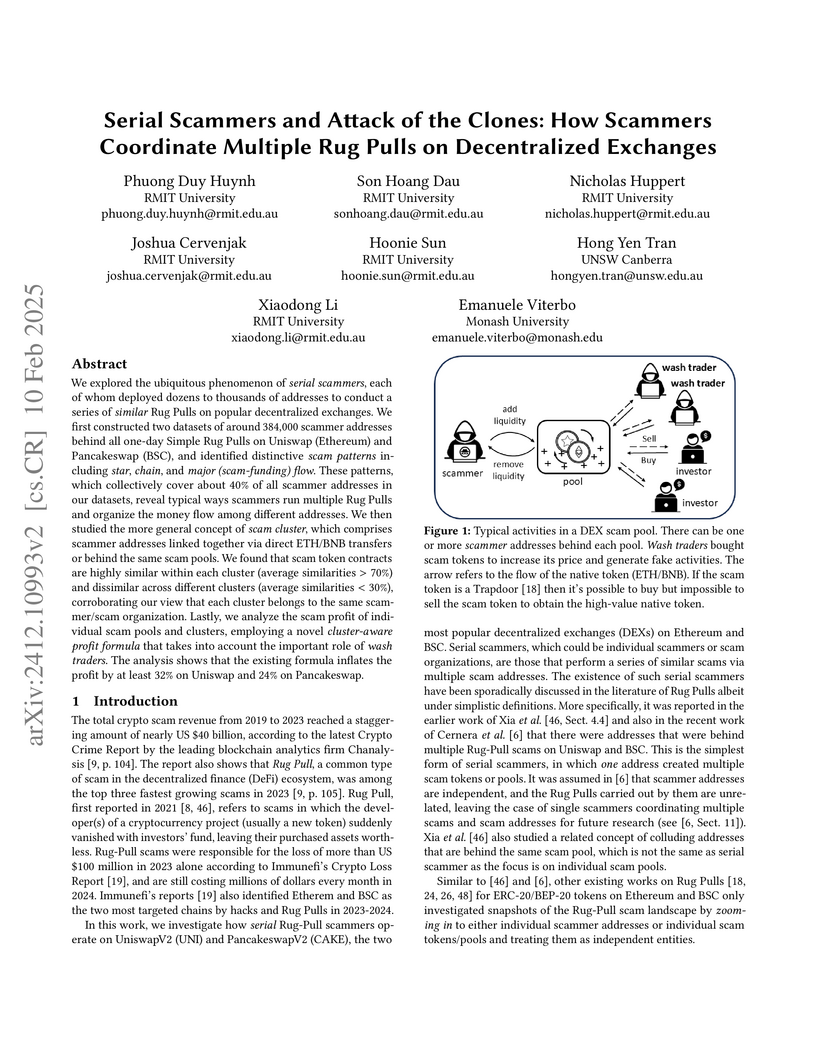
We explored the ubiquitous phenomenon of serial scammers, each of whom
deployed dozens to thousands of addresses to conduct a series of similar Rug
Pulls on popular decentralized exchanges. We first constructed two datasets of
around 384,000 scammer addresses behind all one-day Simple Rug Pulls on Uniswap
(Ethereum) and Pancakeswap (BSC), and identified distinctive scam patterns
including star, chain, and major (scam-funding) flow. These patterns, which
collectively cover about 40% of all scammer addresses in our datasets,
reveal typical ways scammers run multiple Rug Pulls and organize the money flow
among different addresses. We then studied the more general concept of scam
cluster, which comprises scammer addresses linked together via direct ETH/BNB
transfers or behind the same scam pools. We found that scam token contracts are
highly similar within each cluster (average similarities >70\%) and
dissimilar across different clusters (average similarities <30\%),
corroborating our view that each cluster belongs to the same scammer/scam
organization. Lastly, we analyze the scam profit of individual scam pools and
clusters, employing a novel cluster-aware profit formula that takes into
account the important role of wash traders. The analysis shows that the
existing formula inflates the profit by at least 32% on Uniswap and 24%
on Pancakeswap.
This paper examines how distinct cultures of AI interdisciplinarity emerge through interface design, revealing the formation of new disciplinary cultures at these intersections. Through the Interface-Mediated Cognitive Security (IMCS) framework, I demonstrate how the collision of cybersecurity engineering, cognitive psychology, critical technology studies, and human-computer interaction generates research cultures that transcend traditional disciplinary boundaries. AI interfaces function as transformative boundary objects that necessitate methodological fusion rather than mere collaboration, simultaneously embodying technical architectures, psychological design patterns, and social interaction models. Through systematic visual analysis of generative AI platforms and case studies across public sector, medical, and educational domains, I identify four vulnerability vectors, Reflection Simulation, Authority Modulation, Cognitive Load Exploitation, and Market-Security Tension, that structure interface-mediated cognitive security. This research challenges three significant gaps in interdisciplinary theory: the assumption that disciplines maintain distinct methodological boundaries during collaboration, the belief that technical and social knowledge practices can be cleanly separated, and the presumption that disciplinary integration occurs through formal rather than cultural mechanisms. The empirical evidence demonstrates how interfaces function as sites of epistemological collision, creating methodological pressure zones where traditional disciplinary approaches prove insufficient for analysing the complex socio-technical phenomena at the interface.
17 Sep 2020
The review is devoted to a discussion of new (and often unexpected) aspects
of the old problem of elastic light scattering by small metal particles, whose
size is comparable to or smaller than the thickness of the skin layer. The main
focus is put on elucidating the physical grounds for these new aspects. It is
shown that, in many practically important cases, the scattering of light by
such particles, despite their smallness, may have almost nothing in common with
the Rayleigh one. The so-called, anomalous scattering and absorption, as well
as Fano resonances, including unconventional (associated with the excitation of
longitudinal electromagnetic oscillations) and directional Fano resonances,
observed only in a small solid angle, are discussed in detail. The review
contains a Mathematical Supplement, which includes a summary of the main
results of the Mie theory and a discussion of some general properties of the
scattering coefficients. In addition to purely academic interest, the phenomena
considered in this review can find wide applications in biology, medicine,
pharmacology, genetic engineering, imaging of ultra-small objects,
ultra-high-resolution spectroscopy, information transmission, recording, and
processing, and many other applications and technologies. The reported study
was funded by RFBR, project number 19-11-00001 and the project of the Russian
Science Foundation No. 19-72-30012, within the framework of which all the
original calculations given in this publication were performed.
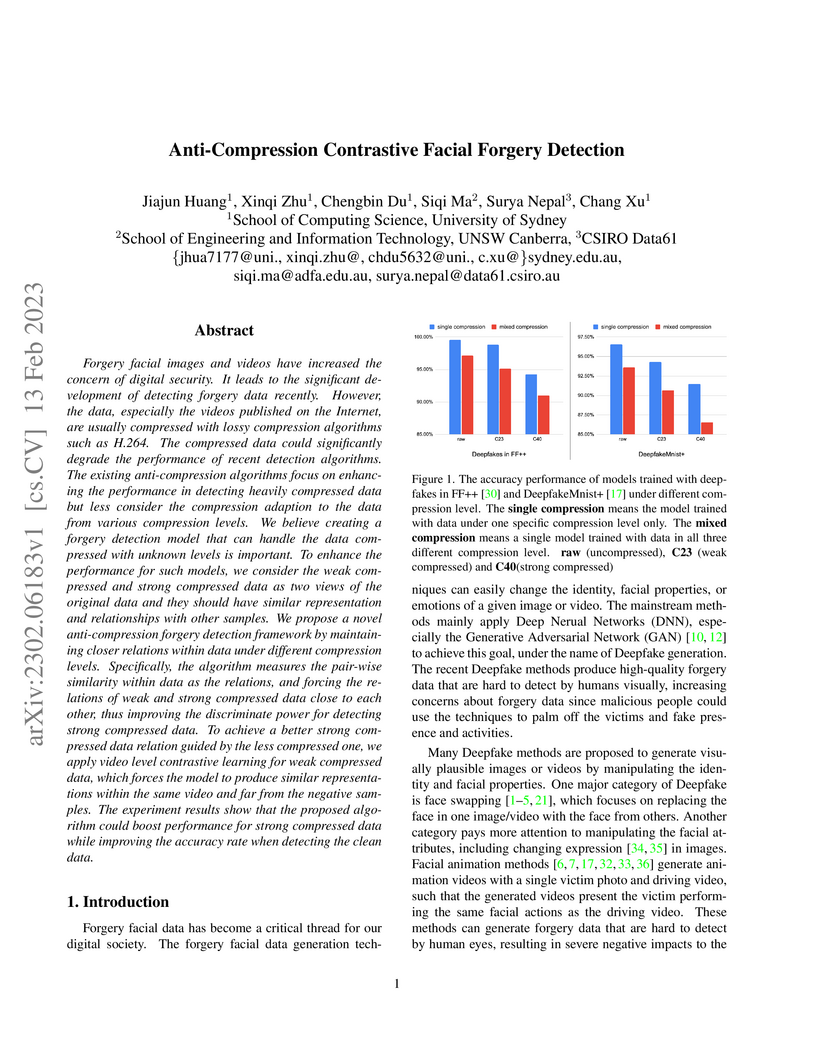
Forgery facial images and videos have increased the concern of digital
security. It leads to the significant development of detecting forgery data
recently. However, the data, especially the videos published on the Internet,
are usually compressed with lossy compression algorithms such as H.264. The
compressed data could significantly degrade the performance of recent detection
algorithms. The existing anti-compression algorithms focus on enhancing the
performance in detecting heavily compressed data but less consider the
compression adaption to the data from various compression levels. We believe
creating a forgery detection model that can handle the data compressed with
unknown levels is important. To enhance the performance for such models, we
consider the weak compressed and strong compressed data as two views of the
original data and they should have similar representation and relationships
with other samples. We propose a novel anti-compression forgery detection
framework by maintaining closer relations within data under different
compression levels. Specifically, the algorithm measures the pair-wise
similarity within data as the relations, and forcing the relations of weak and
strong compressed data close to each other, thus improving the discriminate
power for detecting strong compressed data. To achieve a better strong
compressed data relation guided by the less compressed one, we apply video
level contrastive learning for weak compressed data, which forces the model to
produce similar representations within the same video and far from the negative
samples. The experiment results show that the proposed algorithm could boost
performance for strong compressed data while improving the accuracy rate when
detecting the clean data.
19 Aug 2018
Human-swarm interaction (HSI) involves a number of human factors impacting
human behaviour throughout the interaction. As the technologies used within HSI
advance, it is more tempting to increase the level of swarm autonomy within the
interaction to reduce the workload on humans. Yet, the prospective negative
effects of high levels of autonomy on human situational awareness can hinder
this process. Flexible autonomy aims at trading-off these effects by changing
the level of autonomy within the interaction when required; with
mixed-initiatives combining human preferences and automation's recommendations
to select an appropriate level of autonomy at a certain point of time. However,
the effective implementation of mixed-initiative systems raises fundamental
questions on how to combine human preferences and automation recommendations,
how to realise the selected level of autonomy, and what the future impacts on
the cognitive states of a human are. We explore open challenges that hamper the
process of developing effective flexible autonomy. We then highlight the
potential benefits of using system modelling techniques in HSI by illustrating
how they provide HSI designers with an opportunity to evaluate different
strategies for assessing the state of the mission and for adapting the level of
autonomy within the interaction to maximise mission success metrics.
22 Nov 2016
A number of recent works employ bilinear Hamiltonian interactions between Linear Quantum Stochastic Systems (LQSSs). Contrary to naturally occurring Hamiltonian interactions between physical systems, such interactions must be engineered. In this work, we propose a simple model for the implementation of an arbitrary bilinear interaction between two given LQSSs via a feedback interconnection.
27 Apr 2018
Given a linear open quantum system which is described by a Lindblad master
equation, we detail the calculation of the moment evolution equations from this
master equation. We stress that the moment evolution equations are well-known,
but their explicit derivation from the master equation cannot be found in the
literature to the best of our knowledge, and so we provide this derivation for
the interested reader.
10 Oct 2018
In apprenticeship learning (AL), agents learn by watching or acquiring human
demonstrations on some tasks of interest. However, the lack of human
demonstrations in novel tasks where they may not be a human expert yet, or when
it is too expensive and/or time consuming to acquire human demonstrations
motivated a new algorithm: Apprenticeship bootstrapping (ABS). The basic idea
is to learn from demonstrations on sub-tasks then autonomously bootstrap a
model on the main, more complex, task. The original ABS used inverse
reinforcement learning (ABS-IRL). However, the approach is not suitable for
continuous action spaces.
In this paper, we propose ABS via Deep learning (ABS-DL). It is first
validated in a simulation environment on an aerial and ground coordination
scenario, where an Unmanned Aerial Vehicle (UAV) is required to maintain three
Unmanned Ground Vehicles (UGVs) within a field of view of the UAV 's camera
(FoV). Moving a machine learning algorithm from a simulation environment to an
actual physical platform is challenging because `mistakes' made by the
algorithm while learning could lead to the damage of the platform. We then take
this extra step to test the algorithm in a physical environment. We propose a
safety-net as a protection layer to ensure that the autonomy of the algorithm
in learning does not compromise the safety of the platform. The tests of ABS-DL
in the real environment can guarantee a damage-free, collision avoidance
behaviour of autonomous bodies. The results show that performance of the
proposed approach is comparable to that of a human, and competitive to the
traditional approach using expert demonstrations performed on the composite
task. The proposed safety-net approach demonstrates its advantages when it
enables the UAV to operate more safely under the control of the ABS-DL
algorithm.
15 Apr 2019
Vorticity in two-dimensional superfluids is subject to intense research efforts due to its role in quantum turbulence, dissipation and the BKT phase transition. Interaction of sound and vortices is of broad importance in Bose-Einstein condensates and superfluid helium [1-4]. However, both the modelling of the vortex flow field and of its interaction with sound are complicated hydrodynamic problems, with analytic solutions only available in special cases. In this work, we develop methods to compute both the vortex and sound flow fields in an arbitrary two-dimensional domain. Further, we analyse the dispersive interaction of vortices with sound modes in a two-dimensional superfluid and develop a model that quantifies this interaction for any vortex distribution on any two-dimensional bounded domain, possibly non-simply connected, exploiting analogies with fluid dynamics of an ideal gas and electrostatics. As an example application we use this technique to propose an experiment that should be able to unambiguously detect single circulation quanta in a helium thin film.
08 Jul 2023
Utilizing Low Earth Orbit (LEO) satellite networks equipped with
Inter-Satellite Links (ISL) is envisioned to provide lower delay compared to
traditional optical networks. However, LEO satellites have constrained energy
resources as they rely on solar energy in their operations. Thus requiring
special consideration when designing network topologies that do not only have
low-delay link paths but also low-power consumption. In this paper, we study
different satellite constellation types and network typologies and propose a
novel power-efficient topology. As such, we compare three common satellite
architectures, namely; (i) the theoretical random constellation, the widely
deployed (ii) Walker-Delta, and (iii) Walker-Star constellations. The
comparison is performed based on both the power efficiency and end-to-end
delay. The results show that the proposed algorithm outperforms long-haul ISL
paths in terms of energy efficiency with only a slight hit to delay performance
relative to the conventional ISL topology.
08 Oct 2019
There exists an increasing demand for a flexible and computationally efficient controller for micro aerial vehicles (MAVs) due to a high degree of environmental perturbations. In this work, an evolving neuro-fuzzy controller, namely Parsimonious Controller (PAC) is proposed. It features fewer network parameters than conventional approaches due to the absence of rule premise parameters. PAC is built upon a recently developed evolving neuro-fuzzy system known as parsimonious learning machine (PALM) and adopts new rule growing and pruning modules derived from the approximation of bias and variance. These rule adaptation methods have no reliance on user-defined thresholds, thereby increasing the PAC's autonomy for real-time deployment. PAC adapts the consequent parameters with the sliding mode control (SMC) theory in the single-pass fashion. The boundedness and convergence of the closed-loop control system's tracking error and the controller's consequent parameters are confirmed by utilizing the LaSalle-Yoshizawa theorem. Lastly, the controller's efficacy is evaluated by observing various trajectory tracking performance from a bio-inspired flapping-wing micro aerial vehicle (BI-FWMAV) and a rotary wing micro aerial vehicle called hexacopter. Furthermore, it is compared to three distinctive controllers. Our PAC outperforms the linear PID controller and feed-forward neural network (FFNN) based nonlinear adaptive controller. Compared to its predecessor, G-controller, the tracking accuracy is comparable, but the PAC incurs significantly fewer parameters to attain similar or better performance than the G-controller.
06 Aug 2024
The paper presents a new analysis and a new interpretation of oscillations
observed in the experiments of near wakes of cylinders at Mach 4 and Mach 6 and
Reynolds number range 2 × 104 to 5 × 105 by
\cite{schmidt2015oscillations} and \cite{thasu2022strouhal}. It is shown that
the presence of such oscillations is strongly Reynolds number dependent. It is
further shown that there is a threshold Reynolds number below which wake
unsteadiness and oscillations do not appear. Attention is drawn to the earlier
experimental investigation of supersonic wakes behind cylinders and spheres by
\cite{kendall1962exp} which discusses cylinder oscillations and confirms the
concept of threshold Reynolds number. Following the earlier work of
\cite{goldburg1965strouhal} on hypersonic wakes of spheres and cones, a
Strouhal number(Stθ) based on total wake momentum thickness (θ)
is shown to be the relevant similarity parameter for correlating the hypersonic
and high supersonic wakes of spheres, cones, as well as cylinders. In this
limited sense, Stθ can be said to be `universal'. A universal Strouhal
number based on only one geometry (\textit{i.e.,} a circular cylinder) and over
a limited Reynolds number range as proposed by \cite{schmidt2015oscillations}
is much too restrictive.
27 Feb 2025
Over the last decade, fluvial plastics have been identified as major threat
to aquatic environments and human health. In order to develop adequate
mitigation strategies for plastic pollution, a fundamental process
understanding of riverine plastic transport is of significant importance. In
this context, the implementation of research findings into numerical simulation
environments is anticipated to enhance modelling capabilities and to support a
rigorous decision making. Recent experimental research has focused on the
incipient motion of plastic particles, as well as on the effects of surface
tension on plastic concentration profiles. While these investigations have
advanced the state-of-the-art knowledge, current literature still displays a
lack of basic insights into layer-specific plastic transport physics. In this
study, first principles are applied to advance knowledge on free-surface
detachment and bed entrainment of fluvial plastics. A novel relationship for
the critical surface detachment velocity is derived, followed by the
development of a framework that allows to relate plastic Shields parameters to
those of natural sediments. Overall, it is anticipated that these developments
will trigger new research within the plastics community, and it is hoped that
present findings will be implemented into Lagrangian particle tracking
software.
Over the Nullarbor Plain in South Australia, the Desert Fireball Network
detected a fireball on the night of 1 June 2019 (7:30 pm local time), and six
weeks later recovered a single meteorite (42 g) named Arpu Kuilpu. This
meteorite was then distributed to a consortium of collaborating institutions to
be measured and analyzed by a number of methodologies including: SEM-EDS, EPMA,
ICP-MS, gamma-ray spectrometry, ideal gas pycnometry, magnetic susceptibility
measurement, {\mu}CT, optical microscopy, and accelerator and noble gas mass
spectrometry techniques. These analyses revealed that Arpu Kuilpu is an
unbrecciated H5 ordinary chondrite, with minimal weathering (W0-1) and minimal
shock (S2). The olivine and pyroxene mineral compositions (in mol%) are Fa:
19.2 +- 0.2, and Fs: 16.8 +- 0.2, further supporting the H5 type and class. The
measured oxygen isotopes are also consistent with an H chondrite ({\delta}17O =
2.904 +- 0.177; {\delta}18O = 4.163 +- 0.336; {\Delta}17O = 0.740 +- 0.002).
Ideal gas pycnometry measured bulk and grain densities of 3.66 +- 0.02 and 3.77
+- 0.02 g cm-3, respectively, yielding a porosity of 3.0 % +- 0.7. The magnetic
susceptibility of this meteorite is log X = 5.16 +- 0.08. The most recent
impact-related heating event experienced by Arpu Kuilpu was measured by
40Ar/39Ar chronology to be 4467 +- 16 Ma, while the cosmic ray exposure age is
estimated to be between 6-8 Ma. The noble gas isotopes, radionuclides, and
fireball observations all indicate that Arpu Kuilpu's meteoroid was quite small
(maximum radius of 10 cm, though more likely between 1-5 cm). Although this
meteorite is a rather ordinary ordinary chondrite, its prior orbit resembled
that of a Jupiter Family Comet (JFC) further lending support to the assertion
that many cm- to m-sized objects on JFC orbits are asteroidal rather than
cometary in origin.
In this paper, the problem of load uncertainty in compliance problems is addressed where the uncertainty is described in the form of a set of finitely many loading scenarios. Computationally more efficient methods are proposed to exactly evaluate and differentiate: 1) the mean compliance, or 2) any scalar-valued function of the individual load compliances such as the weighted sum of the mean and standard deviation. The computational time complexities of all the proposed algorithms are analyzed, compared with the naive approaches and then experimentally verified. Finally, a mean compliance minimization problem, a risk-averse compliance minimization problem and a maximum compliance constrained problem are solved to showcase the efficacy of the proposed algorithms. The maximum compliance constrained problem is solved using the augmented Lagrangian method and the method proposed for handling scalar-valued functions of the load compliances, where the scalar-valued function is the augmented Lagrangian function.
There are no more papers matching your filters at the moment.