State Key Laboratory of Mathematical Engineering and Advanced Computing
Heterogeneous hardware and dynamic workloads worsen long-standing OS bottlenecks in scalability, adaptability, and manageability. At the same time, advances in machine learning (ML), large language models (LLMs), and agent-based methods enable automation and self-optimization, but current efforts lack a unifying view. This survey reviews techniques, architectures, applications, challenges, and future directions at the AI-OS intersection. We chart the shift from heuristic- and rule-based designs to AI-enhanced systems, outlining the strengths of ML, LLMs, and agents across the OS stack. We summarize progress in AI for OS (core components and the wider ecosystem) and in OS for AI (component- and architecture-level support for short- and long-context inference, distributed training, and edge inference). For practice, we consolidate evaluation dimensions, methodological pipelines, and patterns that balance real-time constraints with predictive accuracy. We identify key challenges, such as complexity, overhead, model drift, limited explainability, and privacy and safety risks, and recommend modular, AI-ready kernel interfaces; unified toolchains and benchmarks; hybrid rules-plus-AI decisions with guardrails; and verifiable in-kernel inference. Finally, we propose a three-stage roadmap including AI-powered, AI-refactored, and AI-driven OSs, to bridge prototypes and production and to enable scalable, reliable AI deployment.
Recently, a novel form of audio partial forgery has posed challenges to its forensics, requiring advanced countermeasures to detect subtle forgery manipulations within long-duration audio. However, existing countermeasures still serve a classification purpose and fail to perform meaningful analysis of the start and end timestamps of partial forgery segments. To address this challenge, we introduce a novel coarse-to-fine proposal refinement framework (CFPRF) that incorporates a frame-level detection network (FDN) and a proposal refinement network (PRN) for audio temporal forgery detection and localization. Specifically, the FDN aims to mine informative inconsistency cues between real and fake frames to obtain discriminative features that are beneficial for roughly indicating forgery regions. The PRN is responsible for predicting confidence scores and regression offsets to refine the coarse-grained proposals derived from the FDN. To learn robust discriminative features, we devise a difference-aware feature learning (DAFL) module guided by contrastive representation learning to enlarge the sensitive differences between different frames induced by minor manipulations. We further design a boundary-aware feature enhancement (BAFE) module to capture the contextual information of multiple transition boundaries and guide the interaction between boundary information and temporal features via a cross-attention mechanism. Extensive experiments show that our CFPRF achieves state-of-the-art performance on various datasets, including LAV-DF, ASVS2019PS, and HAD.
With the increasing prevalence of diffusion-based malicious image manipulation, existing proactive defense methods struggle to safeguard images against tampering under unknown conditions. To address this, we propose Anti-Inpainting, a proactive defense approach that achieves protection comprising three novel modules. First, we introduce a multi-level deep feature extractor to obtain intricate features from the diffusion denoising process, enhancing protective effectiveness. Second, we design a multi-scale, semantic-preserving data augmentation technique to enhance the transferability of adversarial perturbations across unknown conditions. Finally, we propose a selection-based distribution deviation optimization strategy to bolster protection against manipulations guided by diverse random seeds. Extensive experiments on InpaintGuardBench and CelebA-HQ demonstrate that Anti-Inpainting effectively defends against diffusion-based inpainters under unknown conditions. Additionally, our approach demonstrates robustness against various image purification methods and transferability across different diffusion model versions.
The success of face recognition (FR) systems has led to serious privacy concerns due to potential unauthorized surveillance and user tracking on social networks. Existing methods for enhancing privacy fail to generate natural face images that can protect facial privacy. In this paper, we propose diffusion-based adversarial identity manipulation (DiffAIM) to generate natural and highly transferable adversarial faces against malicious FR systems. To be specific, we manipulate facial identity within the low-dimensional latent space of a diffusion model. This involves iteratively injecting gradient-based adversarial identity guidance during the reverse diffusion process, progressively steering the generation toward the desired adversarial faces. The guidance is optimized for identity convergence towards a target while promoting semantic divergence from the source, facilitating effective impersonation while maintaining visual naturalness. We further incorporate structure-preserving regularization to preserve facial structure consistency during manipulation. Extensive experiments on both face verification and identification tasks demonstrate that compared with the state-of-the-art, DiffAIM achieves stronger black-box attack transferability while maintaining superior visual quality. We also demonstrate the effectiveness of the proposed approach for commercial FR APIs, including Face++ and Aliyun.
04 Dec 2025
The CoCo framework significantly enhances repository-level code completion by guiding Large Language Models (LLMs) with a multi-granularity understanding of code context, outperforming state-of-the-art Retrieval-Augmented Generation (RAG) methods across various benchmarks and LLM backbones with a negligible increase in latency.
Audio temporal forgery localization (ATFL) aims to find the precise forgery
regions of the partial spoof audio that is purposefully modified. Existing ATFL
methods rely on training efficient networks using fine-grained annotations,
which are obtained costly and challenging in real-world scenarios. To meet this
challenge, in this paper, we propose a progressive audio-language co-learning
network (LOCO) that adopts co-learning and self-supervision manners to prompt
localization performance under weak supervision scenarios. Specifically, an
audio-language co-learning module is first designed to capture forgery
consensus features by aligning semantics from temporal and global perspectives.
In this module, forgery-aware prompts are constructed by using utterance-level
annotations together with learnable prompts, which can incorporate semantic
priors into temporal content features dynamically. In addition, a forgery
localization module is applied to produce forgery proposals based on fused
forgery-class activation sequences. Finally, a progressive refinement strategy
is introduced to generate pseudo frame-level labels and leverage supervised
semantic contrastive learning to amplify the semantic distinction between real
and fake content, thereby continuously optimizing forgery-aware features.
Extensive experiments show that the proposed LOCO achieves SOTA performance on
three public benchmarks.
Researchers from Chinese universities developed U3-Attack, a universal and input-agnostic multimodal jailbreak framework that bypasses Text-to-Image (T2I) model safeguards, including prompt filters and image safety checkers. The attack achieves up to 98.361% attack success rate against open-source safety checkers and demonstrates substantial improvements over prior methods on commercial T2I platforms like Runway, Leonardo.Ai, and DALL·E 3.
The task of Detecting and Grounding Multi-Modal Media Manipulation (DGM4) is a branch of misinformation detection. Unlike traditional binary classification, it includes complex subtasks such as forgery content localization and forgery method classification. Consider that existing methods are often limited in performance due to neglecting the erroneous interference caused by unreliable unimodal data and failing to establish comprehensive forgery supervision for mining fine-grained tampering traces. In this paper, we present a Fine-grained Multiple Supervisory (FMS) network, which incorporates modality reliability supervision, unimodal internal supervision and cross-modal supervision to provide comprehensive guidance for DGM4 detection. For modality reliability supervision, we propose the Multimodal Decision Supervised Correction (MDSC) module. It leverages unimodal weak supervision to correct the multi-modal decision-making process. For unimodal internal supervision, we propose the Unimodal Forgery Mining Reinforcement (UFMR) module. It amplifies the disparity between real and fake information within unimodal modality from both feature-level and sample-level perspectives. For cross-modal supervision, we propose the Multimodal Forgery Alignment Reasoning (MFAR) module. It utilizes soft-attention interactions to achieve cross-modal feature perception from both consistency and inconsistency perspectives, where we also design the interaction constraints to ensure the interaction quality. Extensive experiments demonstrate the superior performance of our FMS compared to state-of-the-art methods.
With the rapid rise of large models, copyright protection for generated image
content has become a critical security challenge. Although deep learning
watermarking techniques offer an effective solution for digital image copyright
protection, they still face limitations in terms of visual quality, robustness
and generalization. To address these issues, this paper proposes an adaptive
robust iterative watermarking framework (ARIW-Framework) that achieves
high-quality watermarked images while maintaining exceptional robustness and
generalization performance. Specifically, we introduce an iterative approach to
optimize the encoder for generating robust residuals. The encoder incorporates
noise layers and a decoder to compute robustness weights for residuals under
various noise attacks. By employing a parallel optimization strategy, the
framework enhances robustness against multiple types of noise attacks.
Furthermore, we leverage image gradients to determine the embedding strength at
each pixel location, significantly improving the visual quality of the
watermarked images. Extensive experiments demonstrate that the proposed method
achieves superior visual quality while exhibiting remarkable robustness and
generalization against noise attacks.
Talking face generation (TFG) allows for producing lifelike talking videos of
any character using only facial images and accompanying text. Abuse of this
technology could pose significant risks to society, creating the urgent need
for research into corresponding detection methods. However, research in this
field has been hindered by the lack of public datasets. In this paper, we
construct the first large-scale multi-scenario talking face dataset (MSTF),
which contains 22 audio and video forgery techniques, filling the gap of
datasets in this field. The dataset covers 11 generation scenarios and more
than 20 semantic scenarios, closer to the practical application scenario of
TFG. Besides, we also propose a TFG detection framework, which leverages the
analysis of both global and local coherence in the multimodal content of TFG
videos. Therefore, a region-focused smoothness detection module (RSFDM) and a
discrepancy capture-time frame aggregation module (DCTAM) are introduced to
evaluate the global temporal coherence of TFG videos, aggregating multi-grained
spatial information. Additionally, a visual-audio fusion module (V-AFM) is
designed to evaluate audiovisual coherence within a localized temporal
perspective. Comprehensive experiments demonstrate the reasonableness and
challenges of our datasets, while also indicating the superiority of our
proposed method compared to the state-of-the-art deepfake detection approaches.
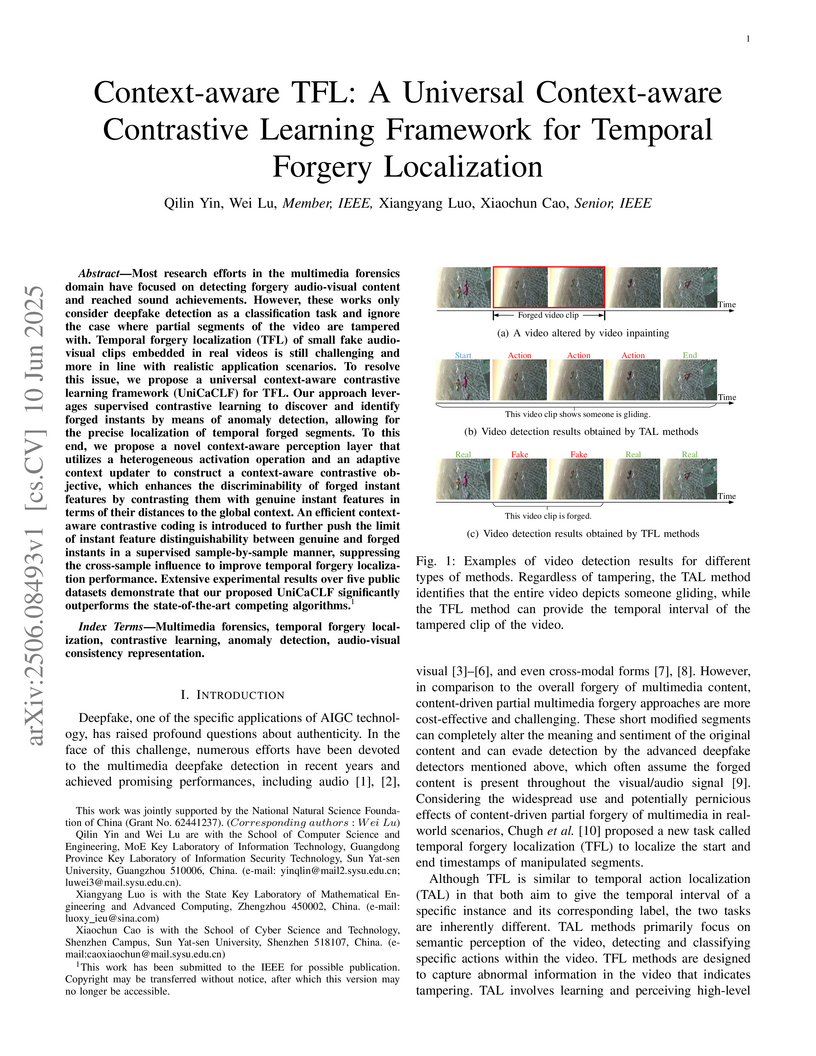
Most research efforts in the multimedia forensics domain have focused on
detecting forgery audio-visual content and reached sound achievements. However,
these works only consider deepfake detection as a classification task and
ignore the case where partial segments of the video are tampered with. Temporal
forgery localization (TFL) of small fake audio-visual clips embedded in real
videos is still challenging and more in line with realistic application
scenarios. To resolve this issue, we propose a universal context-aware
contrastive learning framework (UniCaCLF) for TFL. Our approach leverages
supervised contrastive learning to discover and identify forged instants by
means of anomaly detection, allowing for the precise localization of temporal
forged segments. To this end, we propose a novel context-aware perception layer
that utilizes a heterogeneous activation operation and an adaptive context
updater to construct a context-aware contrastive objective, which enhances the
discriminability of forged instant features by contrasting them with genuine
instant features in terms of their distances to the global context. An
efficient context-aware contrastive coding is introduced to further push the
limit of instant feature distinguishability between genuine and forged instants
in a supervised sample-by-sample manner, suppressing the cross-sample influence
to improve temporal forgery localization performance. Extensive experimental
results over five public datasets demonstrate that our proposed UniCaCLF
significantly outperforms the state-of-the-art competing algorithms.
Deep learning frameworks such as TensorFlow and PyTorch provide a productive interface for expressing and training a deep neural network (DNN) model on a single device or using data parallelism. Still, they may not be flexible or efficient enough in training emerging large models on distributed devices, which require more sophisticated parallelism beyond data parallelism. Plugins or wrappers have been developed to strengthen these frameworks for model or pipeline parallelism, but they complicate the usage and implementation of distributed deep learning. Aiming at a simple, neat redesign of distributed deep learning frameworks for various parallelism paradigms, we present OneFlow, a novel distributed training framework based on an SBP (split, broadcast and partial-value) abstraction and the actor model. SBP enables much easier programming of data parallelism and model parallelism than existing frameworks, and the actor model provides a succinct runtime mechanism to manage the complex dependencies imposed by resource constraints, data movement and computation in distributed deep learning. We demonstrate the general applicability and efficiency of OneFlow for training various large DNN models with case studies and extensive experiments. The results show that OneFlow outperforms many well-known customized libraries built on top of the state-of-the-art frameworks. The code of OneFlow is available at: this https URL.
The spread of Deepfake videos has caused a trust crisis and impaired social stability. Although numerous approaches have been proposed to address the challenges of Deepfake detection and localization, there is still a lack of systematic research on the weakly supervised multimodal fine-grained temporal forgery localization (WS-MTFL). In this paper, we propose a novel weakly supervised multimodal temporal forgery localization via multitask learning (WMMT), which addresses the WS-MTFL under the multitask learning paradigm. WMMT achieves multimodal fine-grained Deepfake detection and temporal partial forgery localization using merely video-level annotations. Specifically, visual and audio modality detection are formulated as two binary classification tasks. The multitask learning paradigm is introduced to integrate these tasks into a multimodal task. Furthermore, WMMT utilizes a Mixture-of-Experts structure to adaptively select appropriate features and localization head, achieving excellent flexibility and localization precision in WS-MTFL. A feature enhancement module with temporal property preserving attention mechanism is proposed to identify the intra- and inter-modality feature deviation and construct comprehensive video features. To further explore the temporal information for weakly supervised learning, an extensible deviation perceiving loss has been proposed, which aims to enlarge the deviation of adjacent segments of the forged samples and reduce the deviation of genuine samples. Extensive experiments demonstrate the effectiveness of multitask learning for WS-MTFL, and the WMMT achieves comparable results to fully supervised approaches in several evaluation metrics.
23 Dec 2022
A quantum algorithm leverages a quantum approximate optimization algorithm (QAOA) to enhance a classical lattice-reduction-based factoring method, enabling the factorization of a 48-bit integer using 10 superconducting qubits. This approach demonstrates sublinear qubit scaling, estimating that an RSA-2048 number could be factored with 372 physical qubits.
Current researches on Deepfake forensics often treat detection as a classification task or temporal forgery localization problem, which are usually restrictive, time-consuming, and challenging to scale for large datasets. To resolve these issues, we present a multimodal deviation perceiving framework for weakly-supervised temporal forgery localization (MDP), which aims to identify temporal partial forged segments using only video-level annotations. The MDP proposes a novel multimodal interaction mechanism (MI) and an extensible deviation perceiving loss to perceive multimodal deviation, which achieves the refined start and end timestamps localization of forged segments. Specifically, MI introduces a temporal property preserving cross-modal attention to measure the relevance between the visual and audio modalities in the probabilistic embedding space. It could identify the inter-modality deviation and construct comprehensive video features for temporal forgery localization. To explore further temporal deviation for weakly-supervised learning, an extensible deviation perceiving loss has been proposed, aiming at enlarging the deviation of adjacent segments of the forged samples and reducing that of genuine samples. Extensive experiments demonstrate the effectiveness of the proposed framework and achieve comparable results to fully-supervised approaches in several evaluation metrics.
VoiceCloak: A Multi-Dimensional Defense Framework against Unauthorized Diffusion-based Voice Cloning
VoiceCloak: A Multi-Dimensional Defense Framework against Unauthorized Diffusion-based Voice Cloning
Diffusion Models (DMs) have achieved remarkable success in realistic voice cloning (VC), while they also increase the risk of malicious misuse. Existing proactive defenses designed for traditional VC models aim to disrupt the forgery process, but they have been proven incompatible with DMs due to the intricate generative mechanisms of diffusion. To bridge this gap, we introduce VoiceCloak, a multi-dimensional proactive defense framework with the goal of obfuscating speaker identity and degrading perceptual quality in potential unauthorized VC. To achieve these goals, we conduct a focused analysis to identify specific vulnerabilities within DMs, allowing VoiceCloak to disrupt the cloning process by introducing adversarial perturbations into the reference audio. Specifically, to obfuscate speaker identity, VoiceCloak first targets speaker identity by distorting representation learning embeddings to maximize identity variation, which is guided by auditory perception principles. Additionally, VoiceCloak disrupts crucial conditional guidance processes, particularly attention context, thereby preventing the alignment of vocal characteristics that are essential for achieving convincing cloning. Then, to address the second objective, VoiceCloak introduces score magnitude amplification to actively steer the reverse trajectory away from the generation of high-quality speech. Noise-guided semantic corruption is further employed to disrupt structural speech semantics captured by DMs, degrading output quality. Extensive experiments highlight VoiceCloak's outstanding defense success rate against unauthorized diffusion-based voice cloning. Audio samples of VoiceCloak are available at this https URL.
Researchers developed the Open-World Deepfake Detection Generalization Enhancement Training Strategy (OWG-DS), an unsupervised domain adaptation approach that enhances deepfake detection generalization to unseen manipulation methods. This method improves cross-dataset detection performance, achieving AUC scores up to 97.31% while requiring minimal labeled data from new domains.
LLMEmbed introduces a transfer learning paradigm that leverages the semantic embedding capabilities of lightweight Large Language Models (LLMs) for text classification. The method achieves high accuracy comparable to much larger, more expensive models like GPT-3, while significantly reducing computational overhead, runtime, and cost by avoiding complex prompt-based generation.
Convolutional neural networks have outperformed humans in image recognition tasks, but they remain vulnerable to attacks from adversarial examples. Since these data are crafted by adding imperceptible noise to normal images, their existence poses potential security threats to deep learning systems. Sophisticated adversarial examples with strong attack performance can also be used as a tool to evaluate the robustness of a model. However, the success rate of adversarial attacks can be further improved in black-box environments. Therefore, this study combines a modified Adam gradient descent algorithm with the iterative gradient-based attack method. The proposed Adam Iterative Fast Gradient Method is then used to improve the transferability of adversarial examples. Extensive experiments on ImageNet showed that the proposed method offers a higher attack success rate than existing iterative methods. By extending our method, we achieved a state-of-the-art attack success rate of 95.0% on defense models.
Image forgery localization (IFL) is a crucial technique for preventing
tampered image misuse and protecting social safety. However, due to the rapid
development of image tampering technologies, extracting more comprehensive and
accurate forgery clues remains an urgent challenge. To address these
challenges, we introduce a novel information-theoretic IFL framework named
SUMI-IFL that imposes sufficiency-view and minimality-view constraints on
forgery feature representation. First, grounded in the theoretical analysis of
mutual information, the sufficiency-view constraint is enforced on the feature
extraction network to ensure that the latent forgery feature contains
comprehensive forgery clues. Considering that forgery clues obtained from a
single aspect alone may be incomplete, we construct the latent forgery feature
by integrating several individual forgery features from multiple perspectives.
Second, based on the information bottleneck, the minimality-view constraint is
imposed on the feature reasoning network to achieve an accurate and concise
forgery feature representation that counters the interference of task-unrelated
features. Extensive experiments show the superior performance of SUMI-IFL to
existing state-of-the-art methods, not only on in-dataset comparisons but also
on cross-dataset comparisons.
There are no more papers matching your filters at the moment.