Previous benchmarks on prompt injection in large language models (LLMs) have
primarily focused on generic tasks and attacks, offering limited insights into
more complex threats like data exfiltration. This paper examines how prompt
injection can cause tool-calling agents to leak personal data observed during
task execution. Using a fictitious banking agent, we develop data flow-based
attacks and integrate them into AgentDojo, a recent benchmark for agentic
security. To enhance its scope, we also create a richer synthetic dataset of
human-AI banking conversations. In 16 user tasks from AgentDojo, LLMs show a
15-50 percentage point drop in utility under attack, with average attack
success rates (ASR) around 20 percent; some defenses reduce ASR to zero. Most
LLMs, even when successfully tricked by the attack, avoid leaking highly
sensitive data like passwords, likely due to safety alignments, but they remain
vulnerable to disclosing other personal data. The likelihood of password
leakage increases when a password is requested along with one or two additional
personal details. In an extended evaluation across 48 tasks, the average ASR is
around 15 percent, with no built-in AgentDojo defense fully preventing leakage.
Tasks involving data extraction or authorization workflows, which closely
resemble the structure of exfiltration attacks, exhibit the highest ASRs,
highlighting the interaction between task type, agent performance, and defense
efficacy.
The consequences of noncommutativity of space coordinates of string theory in the proposed large extra dimension solution to the hierarchy problem are explored; in particular the large dimension stabilization and the graviton reabsorption in the brane are considered.
09 Oct 2018
We study the relation between the vanishing of André-Quillen homology and complete intersection flat dimension and we extend some of the existing results in the literature.
09 Mar 2022
 University of WashingtonUniversity of Cincinnati
University of WashingtonUniversity of Cincinnati University of PittsburghUniversity of OsloSLAC National Accelerator Laboratory
University of PittsburghUniversity of OsloSLAC National Accelerator Laboratory Chinese Academy of SciencesDESY
Chinese Academy of SciencesDESY University of ManchesterUniversity of Zurich
University of ManchesterUniversity of Zurich Tel Aviv UniversityKorea University
Tel Aviv UniversityKorea University University College London
University College London University of OxfordNikhef
University of OxfordNikhef University of Science and Technology of China
University of Science and Technology of China University of California, IrvineUniversity of WarsawPennsylvania State University
University of California, IrvineUniversity of WarsawPennsylvania State University Yale UniversitySouthern Methodist University
Yale UniversitySouthern Methodist University CERN
CERN University of Maryland
University of Maryland Brookhaven National Laboratory
Brookhaven National Laboratory University of Wisconsin-Madison
University of Wisconsin-Madison Université Paris-Saclay
Université Paris-Saclay Stockholm UniversityUppsala UniversityDeutsches Elektronen-Synchrotron DESYFermi National Accelerator LaboratoryUniversity of GenevaUniversity of GlasgowUniversität BonnUniversità di Genova
Stockholm UniversityUppsala UniversityDeutsches Elektronen-Synchrotron DESYFermi National Accelerator LaboratoryUniversity of GenevaUniversity of GlasgowUniversität BonnUniversità di Genova University of VirginiaUniversity of SussexUniversity of TsukubaLund UniversityUniversity of the WitwatersrandUniversity of AlabamaUniversité de MonsUniversity of KansasOklahoma State UniversityUniversity of YorkUniversity of the Basque CountryJefferson LabUniversity of AntwerpFederal University of ABCUniversidad de Los AndesUniversity of JyvaskylaNational Centre for Nuclear ResearchIKERBASQUE-Basque Foundation for ScienceUniversity of BariUniversity of DurhamIPMINR RASKIASINFN GenovaIP2I LyonINFN BariUniversidad Tecnica Federico Santa MariaMoscow Institute for Physics and TechnologyUniversity of Texas A&MLPTHE, Sorbonne Université & CNRSIFIC, CSIC-UVUniversit
catholique de LouvainRWTH Aachen University
University of VirginiaUniversity of SussexUniversity of TsukubaLund UniversityUniversity of the WitwatersrandUniversity of AlabamaUniversité de MonsUniversity of KansasOklahoma State UniversityUniversity of YorkUniversity of the Basque CountryJefferson LabUniversity of AntwerpFederal University of ABCUniversidad de Los AndesUniversity of JyvaskylaNational Centre for Nuclear ResearchIKERBASQUE-Basque Foundation for ScienceUniversity of BariUniversity of DurhamIPMINR RASKIASINFN GenovaIP2I LyonINFN BariUniversidad Tecnica Federico Santa MariaMoscow Institute for Physics and TechnologyUniversity of Texas A&MLPTHE, Sorbonne Université & CNRSIFIC, CSIC-UVUniversit
catholique de LouvainRWTH Aachen UniversityHigh energy collisions at the High-Luminosity Large Hadron Collider (LHC) produce a large number of particles along the beam collision axis, outside of the acceptance of existing LHC experiments. The proposed Forward Physics Facility (FPF), to be located several hundred meters from the ATLAS interaction point and shielded by concrete and rock, will host a suite of experiments to probe Standard Model (SM) processes and search for physics beyond the Standard Model (BSM). In this report, we review the status of the civil engineering plans and the experiments to explore the diverse physics signals that can be uniquely probed in the forward region. FPF experiments will be sensitive to a broad range of BSM physics through searches for new particle scattering or decay signatures and deviations from SM expectations in high statistics analyses with TeV neutrinos in this low-background environment. High statistics neutrino detection will also provide valuable data for fundamental topics in perturbative and non-perturbative QCD and in weak interactions. Experiments at the FPF will enable synergies between forward particle production at the LHC and astroparticle physics to be exploited. We report here on these physics topics, on infrastructure, detector, and simulation studies, and on future directions to realize the FPF's physics potential.
Large language models (LLMs) have traditionally relied on static training data, limiting their knowledge to fixed snapshots. Recent advancements, however, have equipped LLMs with web browsing capabilities, enabling real time information retrieval and multi step reasoning over live web content. While prior studies have demonstrated LLMs ability to access and analyze websites, their capacity to directly retrieve and analyze social media data remains unexplored. Here, we evaluate whether web browsing LLMs can infer demographic attributes of social media users given only their usernames. Using a synthetic dataset of 48 X (Twitter) accounts and a survey dataset of 1,384 international participants, we show that these models can access social media content and predict user demographics with reasonable accuracy. Analysis of the synthetic dataset further reveals how LLMs parse and interpret social media profiles, which may introduce gender and political biases against accounts with minimal activity. While this capability holds promise for computational social science in the post API era, it also raises risks of misuse particularly in information operations and targeted advertising underscoring the need for safeguards. We recommend that LLM providers restrict this capability in public facing applications, while preserving controlled access for verified research purposes.
24 Jan 2022
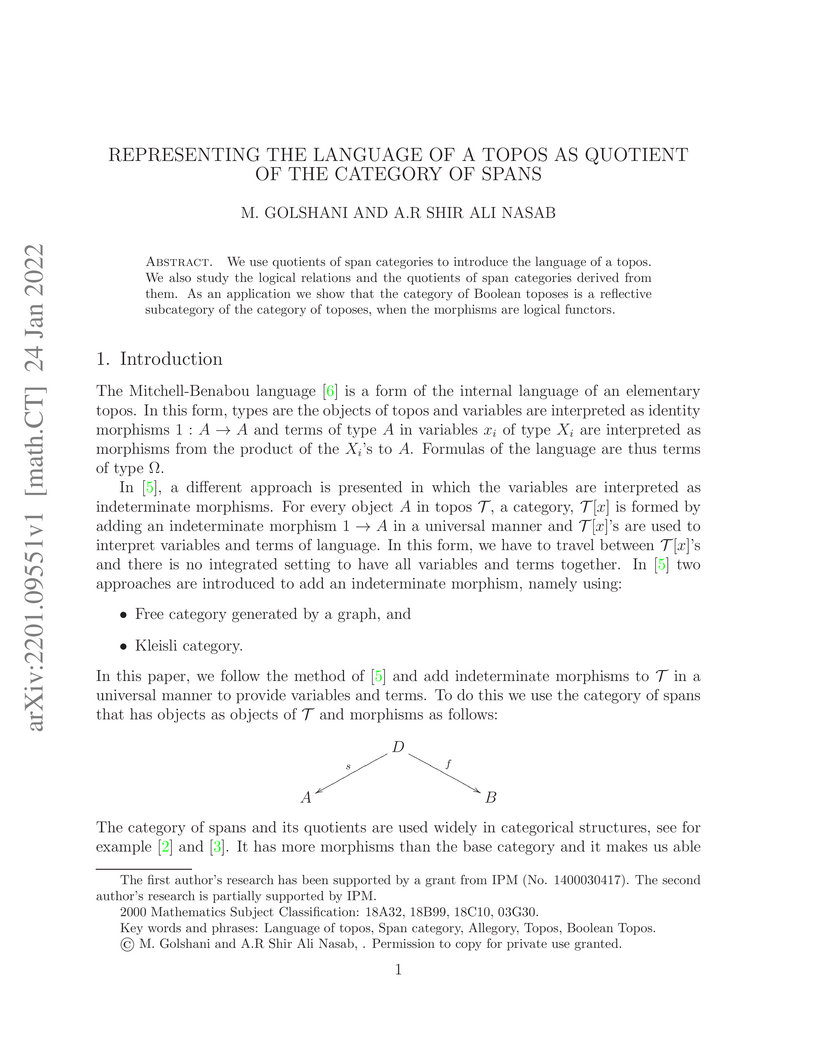
We use quotients of span categories to introduce the language of a topos. We
also study the logical relations and the quotients of span categories derived
from them. As an application we show that the category of Boolean toposes is a
reflective subcategory of the category of toposes, when the morphisms are
logical functors.
26 Jun 2021
The following relaxation of the classical problem of determining Ramsey number of a fixed graph has first been proposed by Erdos, Hajnal and Rado over 50 years ago. Given a graph G and an integer t≥2 determine the minimum number N such that in any t-coloured complete graph on N vertices there is a copy of G using only edges of some t−1 colours. We determine the answer precisely when G is a path.
Using an effective theory for an ensemble of center vortices, we observe the area law fall-off in the continuum limit for the SU(2) gauge group in three-dimensional Euclidean space-time. The string tension is obtained in terms of the intrinsic properties of the vortices and a parameter which describes their interactions. In addition, fitting our analytical results on lattice data, we show that the repulsive force between the vortices increases with temperature. This behavior is expected due to the reduction of vortex configuration at higher temperatures, required for the deconfinement regime.
In this article, we study the Ricci flow neckpinch in the context of metric
measure spaces. We introduce the notion of a Ricci flow metric measure
spacetime and of a weak (refined) super Ricci flow associated to convex cost
functions (cost functions which are increasing convex functions of the distance
function). Our definition of a weak super Ricci flow is based on the coupled
contraction property for suitably defined diffusions on maximal diffusion
components. In our main theorem, we show that if a non-degenerate spherical
neckpinch can be continued beyond the singular time by a smooth forward
evolution then the corresponding Ricci flow metric measure spacetime through
the singularity is a weak super Ricci flow for a (and therefore for all) convex
cost functions if and only if the single point pinching phenomenon holds at
singular times; i.e., if singularities form on a finite number of totally
geodesic hypersurfaces of the form {x}×\spheren. We also show the
spacetime is a refined weak super Ricci flow if and only if the flow is a
smooth Ricci flow with possibly singular final time.
01 Oct 2025
In this paper, we deal with the notions of naturality from category theory and definablity from model theory and their interactions. In this regard, we present three results. First, we show, under some mild conditions, that naturality implies definablity. Second, by using the reverse Easton iteration of Cohen forcing notions, we construct a transitive model of ZFC in which every uniformisable construction is weakly natural. Finally, we show that if F is a natural construction on a class K of structures which is represented by some formula, then it is uniformly definable without any extra parameters. Our results answer some questions by Hodges and Shelah.
25 Apr 2025
We study generically stable types/measures in both classical and continuous
logics, and their connection with randomization and modes of convergence of
types/measures.
12 May 2023
The performance and capacity of solid-state drives (SSDs) are continuously
improving to meet the increasing demands of modern data-intensive applications.
Unfortunately, communication between the SSD controller and memory chips (e.g.,
2D/3D NAND flash chips) is a critical performance bottleneck for many
applications. SSDs use a multi-channel shared bus architecture where multiple
memory chips connected to the same channel communicate to the SSD controller
with only one path. As a result, path conflicts often occur during the
servicing of multiple I/O requests, which significantly limits SSD parallelism.
It is critical to handle path conflicts well to improve SSD parallelism and
performance. Our goal is to fundamentally tackle the path conflict problem by
increasing the number of paths between the SSD controller and memory chips at
low cost. To this end, we build on the idea of using an interconnection network
to increase the path diversity between the SSD controller and memory chips. We
propose Venice, a new mechanism that introduces a low-cost interconnection
network between the SSD controller and memory chips and utilizes the path
diversity to intelligently resolve path conflicts. Venice employs three key
techniques: 1) a simple router chip added next to each memory chip without
modifying the memory chip design, 2) a path reservation technique that reserves
a path from the SSD controller to the target memory chip before initiating a
transfer, and 3) a fully-adaptive routing algorithm that effectively utilizes
the path diversity to resolve path conflicts. Our experimental results show
that Venice 1) improves performance by an average of 2.65x/1.67x over a
baseline performance-optimized/cost-optimized SSD design across a wide range of
workloads, 2) reduces energy consumption by an average of 61% compared to a
baseline performance-optimized SSD design.
06 Oct 2023
Different notions of the consistency of obligations collapse in standard deontic logic. In justification logics, which feature explicit reasons for obligations, the situation is different. Their strength depends on a constant specification and on the available set of operations for combining different reasons. We present different consistency principles in justification logic and compare their logical strength. We propose a novel semantics for which justification logics with the explicit version of axiom D, jd, are complete for arbitrary constant specifications. We then discuss the philosophical implications with regard to some deontic paradoxes.
We generalize a recently introduced formulation of relativistic spinful and
vortical fluid to relativistic magnetohydrodynamics (MHD). We refer to it as
the "Spinful-Vortical MHD" (SVMHD). The aim is to scrutinize the interplay
between the vorticity, magnetic field, and spin, which is treated as a quantum
object, in contrast to other formulations of spin hydrodynamics. To this
purpose, we first perform a standard entropy current analysis up to first-order
gradient expansion, O(∂) as well as
O(ℏ∂), where ℏ is the Planck constant.
In contrast to alternative formulations of spin MHD, in the absence of
vorticity, the zeroth-order energy-momentum tensor includes an additional
magneto-vorticity mixed term and reduces, as expected, to the energy-momentum
tensor of MHD. We show that in the first-order of gradient expansion, 36
dissipative transport coefficients appear. They satisfy certain constraints
that guarantee the positive definiteness of the entropy production rate. We
then modify the formulation of SVMHD by replacing the magnetic part of the
thermal vorticity tensor with its electric part. Carrying out the same analysis
as in the standard formulation, we show that in this case, the first-order
constitutive relations consist of 11 nondissipative Hall-like coefficients,
apart from 25 dissipative coefficients. This difference arises from different
behavior of the electric and magnetic part of the thermal vorticity under
time-reversal transformation.
A possible violation of the weak gravity conjecture (WGC) by cosmic censorship is one of the major challenges in the field of general relativity. However, in this paper, we explore the possibility of reconciling the WGC and the WCCC by considering Reissner-Nordström (R-N) black holes embedded in perfect fluid dark matter (PFDM) in asymptotically flat spacetimes. These two conjectures are seemingly unrelated, but a recent proposal suggested that they are connected surprisingly. In particular, We argue a promising class of valid counterexamples to the WCCC in the four-dimensional Einstein-Maxwell theory, considering a charged black hole when WGC is present. We demonstrate that by imposing certain constraints on the parameters of the metric, the WGC and the WCCC can be compatible. Furthermore, we investigate the properties of the charged black hole in the presence of PFDM for Q>M and present some intriguing figures to test the validity of the WGC and the WCCC simultaneously. When PFDM is absent (γ=0), the RN black hole either has two event horizons if Q2/M2≤1 or none if Q2/M2>1. The second scenario results in a naked singularity, which contradicts the WCCC. But when PFDM is present (γ=0), the RN black hole has event horizons with regard to Q and M. This implies that the singularity is always covered, and the WGC and the WCCC are fulfilled. Furthermore, we demonstrate that there is a critical value of γ, called γext, that makes the RN black hole extremal when γ=γext. In this situation, the black hole has an event horizon, and the WGC and the WCCC are still fulfilled. We infer that PFDM can make the WGC and the WCCC compatible with the RN black hole and that the WGC and the WCCC agree with each other when PFDM is present.
Traffic sampling has become an indispensable tool in network management. While there exists a plethora of sampling systems, they generally assume flow rates are stable and predictable over a sampling period. Consequently, when deployed in networks with dynamic flow rates, some flows may be missed or under-sampled, while others are over-sampled. This paper presents the design and evaluation of dSamp, a network-wide sampling system capable of handling dynamic flow rates in Software-Defined Networks (SDNs). The key idea in dSamp is to consider flow rate fluctuations when deciding on which network switches and at what rate to sample each flow. To this end, we develop a general model for sampling allocation with dynamic flow rates, and then design an efficient approximate integer linear program called APX that can be used to compute sampling allocations even in large-scale networks. To show the efficacy of dSamp for network monitoring, we have implemented APX and several existing solutions in ns-3 and conducted extensive experiments using model-driven as well as trace-driven simulations. Our results indicate that, by considering dynamic flow rates, APX outperforms the existing solutions by up to 10% in sampling more flows at a given sampling rate.
Academics increasingly acknowledge the predictive power of social media for a wide variety of events and, more specifically, for financial markets. Anecdotal and empirical findings show that cryptocurrencies are among the financial assets that have been affected by news and influencers' activities on Twitter. However, the extent to which Twitter crypto influencer's posts about trading signals and their effect on market prices is mostly unexplored. In this paper, we use LLMs to uncover buy and not-buy signals from influencers and news outlets' Twitter posts and use a VAR analysis with Granger Causality tests and cross-correlation analysis to understand how these trading signals are temporally correlated with the top nine major cryptocurrencies' prices. Overall, the results show a mixed pattern across cryptocurrencies and temporal periods. However, we found that for the top three cryptocurrencies with the highest presence within news and influencer posts, their aggregated LLM-detected trading signal over the preceding 24 hours granger-causes fluctuations in their market prices, exhibiting a lag of at least 6 hours. In addition, the results reveal fundamental differences in how influencers and news outlets cover cryptocurrencies.
17 Jan 2025
Suppose κ is a regular cardinal and \bar a=\langle \mu_i: i<\kappa \rangle is a non-decreasing sequence of regular cardinals. We study the set of possible cofinalities of cuts Pcut(aˉ)={(λ1,λ2): for some ultrafilter D on κ, (λ1,λ2) is the cofinality of a cut of \prod\limits_{i<\kappa} \mu_i / D \}.
10 Mar 2025
We present a class of abelian groups that exhibit a high degree of freeness
while possessing no non-trivial homomorphisms to a canonical free object.
Unlike prior investigations, which primarily focused on torsion-free groups,
our work broadens the scope to include groups with torsion. Our main focus is
on reduced separable p-groups, for which we formulate and prove the Trivial
Duality Conjecture. Key tools in our analysis include the multi black-box
method and the application of specific homological properties of relative
trees. These techniques allow us to navigate the intricate interplay between
freeness and duality in a broader class of abelian groups
16 Mar 2025
Let n be a non-negative integer. {Motivated by the universal property of
the stable category of Frobenius categories, the authors in \cite{bfss}
extended the stabilization of Frobenius categories to n-Frobenius categories,
and called it the phantom stable categories. Precisely, assume that \C is an
n-Frobenius category.} The phantom stable category of \C is a pair
(\C\p,T), with \C\p an additive category having the same objects as
\C and T an additive covariant functor from \C to \C\p, vanishing
over n-\Ext-phantom morphisms and T(f) is an isomorphism, for any
n-\Ext-invertible morphism f, {and T has the universal property with
respect to these conditions. The existence of the phantom stable category
(\C\p,T) and its several interesting properties have appeared in
\cite{bfss}. This paper is devoted to further study of phantom stable
categories. In particular, it is shown that } the syzygy functor \syz, using
n-projective objects, from \C to \C\p is not only an additive functor,
but also it induces an auto-equivalence functor \Syz on \C\p. These
results would be the first evidence to show that phantom stable categories are
triangulated, with the shift functor \Syz. At the end of the paper we give a
1-Frobenius subcategory of the category of coherent sheaves over the projective
line.
There are no more papers matching your filters at the moment.