ARM Research
The Transformer architecture has been successful across many domains, including natural language processing, computer vision and speech recognition. In keyword spotting, self-attention has primarily been used on top of convolutional or recurrent encoders. We investigate a range of ways to adapt the Transformer architecture to keyword spotting and introduce the Keyword Transformer (KWT), a fully self-attentional architecture that exceeds state-of-the-art performance across multiple tasks without any pre-training or additional data. Surprisingly, this simple architecture outperforms more complex models that mix convolutional, recurrent and attentive layers. KWT can be used as a drop-in replacement for these models, setting two new benchmark records on the Google Speech Commands dataset with 98.6% and 97.7% accuracy on the 12 and 35-command tasks respectively.
The emergence of latency-critical AI applications has been supported by the
evolution of the edge computing paradigm. However, edge solutions are typically
resource-constrained, posing reliability challenges due to heightened
contention for compute and communication capacities and faulty application
behavior in the presence of overload conditions. Although a large amount of
generated log data can be mined for fault prediction, labeling this data for
training is a manual process and thus a limiting factor for automation. Due to
this, many companies resort to unsupervised fault-tolerance models. Yet,
failure models of this kind can incur a loss of accuracy when they need to
adapt to non-stationary workloads and diverse host characteristics. To cope
with this, we propose a novel modeling approach, called DeepFT, to proactively
avoid system overloads and their adverse effects by optimizing the task
scheduling and migration decisions. DeepFT uses a deep surrogate model to
accurately predict and diagnose faults in the system and co-simulation based
self-supervised learning to dynamically adapt the model in volatile settings.
It offers a highly scalable solution as the model size scales by only 3 and 1
percent per unit increase in the number of active tasks and hosts. Extensive
experimentation on a Raspberry-Pi based edge cluster with DeFog benchmarks
shows that DeepFT can outperform state-of-the-art baseline methods in
fault-detection and QoS metrics. Specifically, DeepFT gives the highest F1
scores for fault-detection, reducing service deadline violations by up to 37\%
while also improving response time by up to 9%.
With the advent of smart devices that support 4K and 8K resolution, Single Image Super Resolution (SISR) has become an important computer vision problem. However, most super resolution deep networks are computationally very expensive. In this paper, we propose Super-Efficient Super Resolution (SESR) networks that establish a new state-of-the-art for efficient super resolution. Our approach is based on linear overparameterization of CNNs and creates an efficient model architecture for SISR. With theoretical analysis, we uncover the limitations of existing overparameterization methods and show how the proposed method alleviates them. Detailed experiments across six benchmark datasets demonstrate that SESR achieves similar or better image quality than state-of-the-art models while requiring 2x to 330x fewer Multiply-Accumulate (MAC) operations. As a result, SESR can be used on constrained hardware to perform x2 (1080p to 4K) and x4 (1080p to 8K) SISR. Towards this, we estimate hardware performance numbers for a commercial Arm mobile-Neural Processing Unit (NPU) for 1080p to 4K (x2) and 1080p to 8K (x4) SISR. Our results highlight the challenges faced by super resolution on AI accelerators and demonstrate that SESR is significantly faster (e.g., 6x-8x higher FPS) than existing models on mobile-NPU. Finally, SESR outperforms prior models by 1.5x-2x in latency on Arm CPU and GPU when deployed on a real mobile device. The code for this work is available at this https URL.
The success of deep learning has brought forth a wave of interest in computer
hardware design to better meet the high demands of neural network inference. In
particular, analog computing hardware has been heavily motivated specifically
for accelerating neural networks, based on either electronic, optical or
photonic devices, which may well achieve lower power consumption than
conventional digital electronics. However, these proposed analog accelerators
suffer from the intrinsic noise generated by their physical components, which
makes it challenging to achieve high accuracy on deep neural networks. Hence,
for successful deployment on analog accelerators, it is essential to be able to
train deep neural networks to be robust to random continuous noise in the
network weights, which is a somewhat new challenge in machine learning. In this
paper, we advance the understanding of noisy neural networks. We outline how a
noisy neural network has reduced learning capacity as a result of loss of
mutual information between its input and output. To combat this, we propose
using knowledge distillation combined with noise injection during training to
achieve more noise robust networks, which is demonstrated experimentally across
different networks and datasets, including ImageNet. Our method achieves models
with as much as two times greater noise tolerance compared with the previous
best attempts, which is a significant step towards making analog hardware
practical for deep learning.
On-device CNN inference for real-time computer vision applications can result
in computational demands that far exceed the energy budgets of mobile devices.
This paper proposes FixyNN, a co-designed hardware accelerator platform which
splits a CNN model into two parts: a set of layers that are fixed in the
hardware platform as a front-end fixed-weight feature extractor, and the
remaining layers which become a back-end classifier running on a conventional
programmable CNN accelerator. The common front-end provides ubiquitous CNN
features for all FixyNN models, while the back-end is programmable and specific
to a given dataset. Image classification models for FixyNN are trained
end-to-end via transfer learning, with front-end layers fixed for the shared
feature extractor, and back-end layers fine-tuned for a specific task. Over a
suite of six datasets, we trained models via transfer learning with an accuracy
loss of <1%, resulting in a FixyNN hardware platform with nearly 2 times better
energy efficiency than a conventional programmable CNN accelerator of the same
silicon area (i.e. hardware cost).
Point cloud analytics is poised to become a key workload on battery-powered embedded and mobile platforms in a wide range of emerging application domains, such as autonomous driving, robotics, and augmented reality, where efficiency is paramount. This paper proposes Mesorasi, an algorithm-architecture co-designed system that simultaneously improves the performance and energy efficiency of point cloud analytics while retaining its accuracy. Our extensive characterizations of state-of-the-art point cloud algorithms show that, while structurally reminiscent of convolutional neural networks (CNNs), point cloud algorithms exhibit inherent compute and memory inefficiencies due to the unique characteristics of point cloud data. We propose delayed-aggregation, a new algorithmic primitive for building efficient point cloud algorithms. Delayed-aggregation hides the performance bottlenecks and reduces the compute and memory redundancies by exploiting the approximately distributive property of key operations in point cloud algorithms. Delayed-aggregation let point cloud algorithms achieve 1.6x speedup and 51.1% energy reduction on a mobile GPU while retaining the accuracy (-0.9% loss to 1.2% gains). To maximize the algorithmic benefits, we propose minor extensions to contemporary CNN accelerators, which can be integrated into a mobile Systems-on-a-Chip (SoC) without modifying other SoC components. With additional hardware support, Mesorasi achieves up to 3.6x speedup.
An important property of concurrent objects is whether they support progress -a special case of liveness-guarantees, which ensure the termination of individual method calls under system fairness assumptions. Liveness properties have been proposed for concurrent objects. Typical liveness properties includelock-freedom,wait-freedom,deadlock-freedom,starvation-freedom and obstruction-freedom. It is known that the five liveness properties above are decidable on the Sequential Consistency (SC) memory model for a bounded number of processes. However, the problem of decidability of liveness for finite state concurrent programs running on relaxed memory models remains open. In this paper we address this problem for the Total Store Order (TSO) memory model,as found in the x86 architecture. We prove that lock-freedom, wait-freedom,deadlock-freedom and starvation-freedom are undecidable on TSO for a bounded number of processes, while obstruction-freedom is decidable.
As Deep Neural Networks (DNNs) are increasingly deployed in safety critical
and privacy sensitive applications such as autonomous driving and biometric
authentication, it is critical to understand the fault-tolerance nature of
DNNs. Prior work primarily focuses on metrics such as Failures In Time (FIT)
rate and the Silent Data Corruption (SDC) rate, which quantify how often a
device fails. Instead, this paper focuses on quantifying the DNN accuracy given
that a transient error has occurred, which tells us how well a network behaves
when a transient error occurs. We call this metric Resiliency Accuracy (RA). We
show that existing RA formulation is fundamentally inaccurate, because it
incorrectly assumes that software variables (model weights/activations) have
equal faulty probability under hardware transient faults. We present an
algorithm that captures the faulty probabilities of DNN variables under
transient faults and, thus, provides correct RA estimations validated by
hardware. To accelerate RA estimation, we reformulate RA calculation as a Monte
Carlo integration problem, and solve it using importance sampling driven by DNN
specific heuristics. Using our lightweight RA estimation method, we show that
transient faults lead to far greater accuracy degradation than what todays DNN
resiliency tools estimate. We show how our RA estimation tool can help design
more resilient DNNs by integrating it with a Network Architecture Search
framework.
In image classification tasks, the evaluation of models' robustness to
increased dataset shifts with a probabilistic framework is very well studied.
However, object detection (OD) tasks pose other challenges for uncertainty
estimation and evaluation. For example, one needs to evaluate both the quality
of the label uncertainty (i.e., what?) and spatial uncertainty (i.e., where?)
for a given bounding box, but that evaluation cannot be performed with more
traditional average precision metrics (e.g., mAP). In this paper, we adapt the
well-established YOLOv3 architecture to generate uncertainty estimations by
introducing stochasticity in the form of Monte Carlo Dropout (MC-Drop), and
evaluate it across different levels of dataset shift. We call this novel
architecture Stochastic-YOLO, and provide an efficient implementation to
effectively reduce the burden of the MC-Drop sampling mechanism at inference
time. Finally, we provide some sensitivity analyses, while arguing that
Stochastic-YOLO is a sound approach that improves different components of
uncertainty estimations, in particular spatial uncertainties.
Sensitive computations are now routinely delegated to third-parties. In response, Confidential Computing technologies are being introduced to microprocessors, offering a protected processing environment, which we generically call an isolate, providing confidentiality and integrity guarantees to code and data hosted within -- even in the face of a privileged attacker. Isolates, with an attestation protocol, permit remote third-parties to establish a trusted "beachhead" containing known code and data on an otherwise untrusted machine. Yet, the rise of these technologies introduces many new problems, including: how to ease provisioning of computations safely into isolates; how to develop distributed systems spanning multiple classes of isolate; and what to do about the billions of "legacy" devices without support for Confidential Computing?
Tackling the problems above, we introduce Veracruz, a framework that eases the design and implementation of complex privacy-preserving, collaborative, delegated computations among a group of mutually mistrusting principals. Veracruz supports multiple isolation technologies and provides a common programming model and attestation protocol across all of them, smoothing deployment of delegated computations over supported technologies. We demonstrate Veracruz in operation, on private in-cloud object detection on encrypted video streaming from a video camera. In addition to supporting hardware-backed isolates -- like AWS Nitro Enclaves and Arm Confidential Computing Architecture Realms -- Veracruz also provides pragmatic "software isolates" on Armv8-A devices without hardware Confidential Computing capability, using the high-assurance seL4 microkernel and our IceCap framework.
04 Aug 2021
Some important problems, such as semantic graph analysis, require large-scale irregular applications composed of many coordinating tasks that operate on a shared data set so big it has to be stored on many physical devices. In these cases, it may be more efficient to dynamically choose where code runs as the applications progresses. Many programming environments provide task migration or remote function calls, but they have sharp trade-offs between flexible composition, portability, performance, and code complexity.
We developed Two-Chains, a high performance framework inspired by active message communication semantics. We use the GNU Binutils, the ELF binary format, and the RDMA network protocol to provide ultra-low granularity distributed function composition at runtime in user space at HPC performance levels using C libraries. Our framework allows the direct injection of function binaries and data to a remote machine cache using the RDMA network. It interoperates seamlessly with existing C libraries using standard dynamic linking and load symbol resolution. We analyze function delivery and execution on cache stashing-enabled hardware and show that stashing decreases latency, increases message rates, and improves noise tolerance. This demonstrates one way this method is suited to increasingly network-oriented hardware architectures.
Massive data exist among user local platforms that usually cannot support
deep neural network (DNN) training due to computation and storage resource
constraints. Cloud-based training schemes provide beneficial services but
suffer from potential privacy risks due to excessive user data collection. To
enable cloud-based DNN training while protecting the data privacy
simultaneously, we propose to leverage the intermediate representations of the
data, which is achieved by splitting the DNNs and deploying them separately
onto local platforms and the cloud. The local neural network (NN) is used to
generate the feature representations. To avoid local training and protect data
privacy, the local NN is derived from pre-trained NNs. The cloud NN is then
trained based on the extracted intermediate representations for the target
learning task. We validate the idea of DNN splitting by characterizing the
dependency of privacy loss and classification accuracy on the local NN topology
for a convolutional NN (CNN) based image classification task. Based on the
characterization, we further propose PrivyNet to determine the local NN
topology, which optimizes the accuracy of the target learning task under the
constraints on privacy loss, local computation, and storage. The efficiency and
effectiveness of PrivyNet are demonstrated with the CIFAR-10 dataset.
02 Dec 2020
As systems and applications grow more complex, detailed simulation takes an
ever increasing amount of time. The prospect of increased simulation time
resulting in slower design iteration forces architects to use simpler models,
such as spreadsheets, when they want to iterate quickly on a design. However,
the task of migrating from a simple simulation to one with more detail often
requires multiple executions to find where simple models could be effective,
which could be more expensive than running the detailed model in the first
place. Also, architects must often rely on intuition to choose these simpler
models, further complicating the problem.
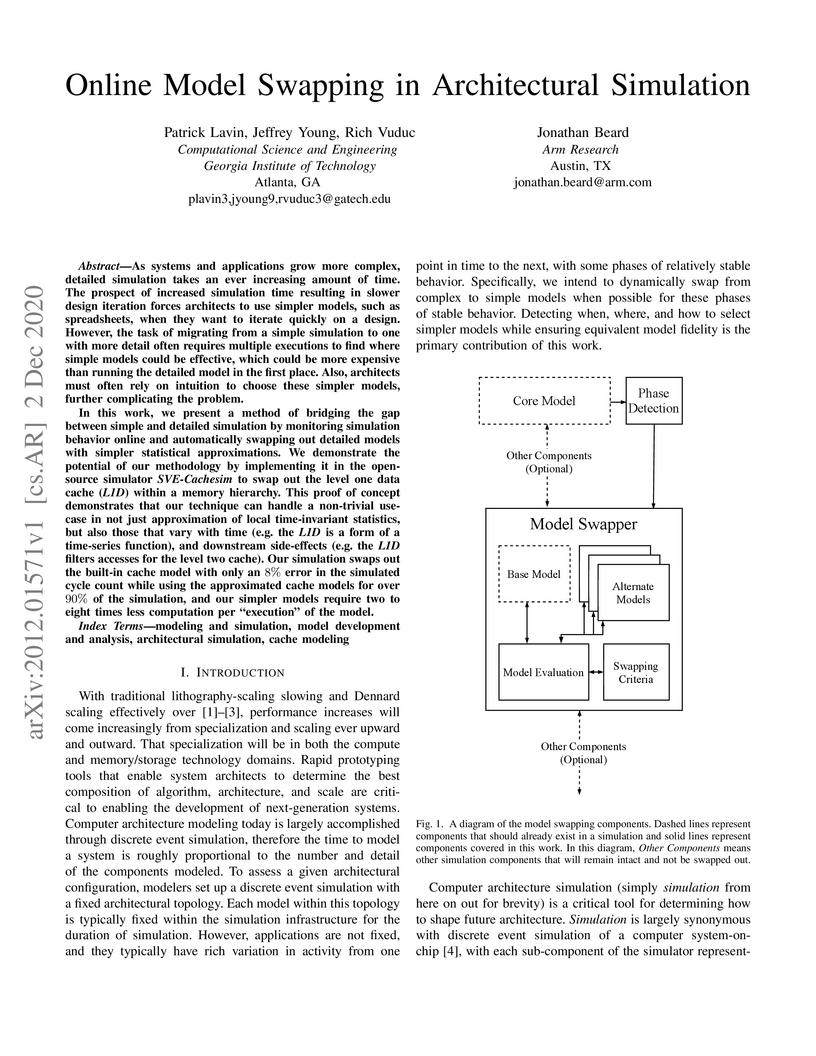
In this work, we present a method of bridging the gap between simple and
detailed simulation by monitoring simulation behavior online and automatically
swapping out detailed models with simpler statistical approximations. We
demonstrate the potential of our methodology by implementing it in the
open-source simulator SVE-Cachesim to swap out the level one data cache (L1D)
within a memory hierarchy. This proof of concept demonstrates that our
technique can handle a non-trivial use-case in not just approximation of local
time-invariant statistics, but also those that vary with time (e.g., the L1D is
a form of a time-series function), and downstream side-effects (e.g., the L1D
filters accesses for the level two cache). Our simulation swaps out the
built-in cache model with only an 8% error in the simulated cycle count while
using the approximated cache models for over 90% of the simulation, and our
simpler models require two to eight times less computation per "execution" of
the model
18 Oct 2021
Modern processors rely heavily on speculation to keep the pipeline filled and consequently execute and commit instructions as close to maximum capacity as possible. To improve instruction-level parallelism, the processor core needs to fetch and decode multiple instructions per cycle and has come to rely on incredibly accurate branch prediction. However, this comes at cost of the increased area and complexity which is needed for modern high accuracy branch predictors.
The key idea described in this work is to use hyperdimensional computing and sparse distributed memory principles to create a novel branch predictor that can deliver complex predictions for a fraction of the current area. Sparse distributed memories can store vast amounts of data in a compressed manner, theoretically enabling branch histories larger and more precise than the branch predictors used today to be stored with equal or smaller area footprint. Furthermore, as all the data is in a hashed format and due to the nature of the hashing scheme used, it is inherently harder to manipulate with known side-channel attacks.
We describe our proof-of-concept and evaluate it against a state-of-the-art academic TAGE predictor. Our experiments are conducted on realistic synthetic branch predictor patterns and the Championship Branch Prediction traces and show competitive accuracy. Finally, we describe techniques that can be used to solve some of the challenges of processing with hyperdimensional vectors in order to deliver timely predictions.
Estimating depth from stereo vision cameras, i.e., "depth from stereo", is
critical to emerging intelligent applications deployed in energy- and
performance-constrained devices, such as augmented reality headsets and mobile
autonomous robots. While existing stereo vision systems make trade-offs between
accuracy, performance and energy-efficiency, we describe ASV, an accelerated
stereo vision system that simultaneously improves both performance and
energy-efficiency while achieving high accuracy. The key to ASV is to exploit
unique characteristics inherent to stereo vision, and apply stereo-specific
optimizations, both algorithmically and computationally. We make two
contributions. Firstly, we propose a new stereo algorithm, invariant-based
stereo matching (ISM), that achieves significant speedup while retaining high
accuracy. The algorithm combines classic "hand-crafted" stereo algorithms with
recent developments in Deep Neural Networks (DNNs), by leveraging the
correspondence invariant unique to stereo vision systems. Secondly, we observe
that the bottleneck of the ISM algorithm is the DNN inference, and in
particular the deconvolution operations that introduce massive
compute-inefficiencies. We propose a set of software optimizations that
mitigate these inefficiencies. We show that with less than 0.5% hardware area
overhead, these algorithmic and computational optimizations can be effectively
integrated within a conventional DNN accelerator. Overall, ASV achieves 5x
speedup and 85% energy saving with 0.02% accuracy loss compared to today
DNN-based stereo vision systems.
Tuning hyperparameters for machine learning algorithms is a tedious task, one
that is typically done manually. To enable automated hyperparameter tuning,
recent works have started to use techniques based on Bayesian optimization.
However, to practically enable automated tuning for large scale machine
learning training pipelines, significant gaps remain in existing libraries,
including lack of abstractions, fault tolerance, and flexibility to support
scheduling on any distributed computing framework. To address these challenges,
we present Mango, a Python library for parallel hyperparameter tuning. Mango
enables the use of any distributed scheduling framework, implements intelligent
parallel search strategies, and provides rich abstractions for defining complex
hyperparameter search spaces that are compatible with scikit-learn. Mango is
comparable in performance to Hyperopt, another widely used library. Mango is
available open-source and is currently used in production at Arm Research to
provide state-of-art hyperparameter tuning capabilities.
As a massive number of the Internet of Things (IoT) devices are deployed, the
security and privacy issues in IoT arouse more and more attention. The IoT
attacks are causing tremendous loss to the IoT networks and even threatening
human safety. Compared to traditional networks, IoT networks have unique
characteristics, which make the attack detection more challenging. First, the
heterogeneity of platforms, protocols, software, and hardware exposes various
vulnerabilities. Second, in addition to the traditional high-rate attacks, the
low-rate attacks are also extensively used by IoT attackers to obfuscate the
legitimate and malicious traffic. These low-rate attacks are challenging to
detect and can persist in the networks. Last, the attackers are evolving to be
more intelligent and can dynamically change their attack strategies based on
the environment feedback to avoid being detected, making it more challenging
for the defender to discover a consistent pattern to identify the attack.
In order to adapt to the new characteristics in IoT attacks, we propose a
reinforcement learning-based attack detection model that can automatically
learn and recognize the transformation of the attack pattern. Therefore, we can
continuously detect IoT attacks with less human intervention. In this paper, we
explore the crucial features of IoT traffics and utilize the entropy-based
metrics to detect both the high-rate and low-rate IoT attacks. Afterward, we
leverage the reinforcement learning technique to continuously adjust the attack
detection threshold based on the detection feedback, which optimizes the
detection and the false alarm rate. We conduct extensive experiments over a
real IoT attack dataset and demonstrate the effectiveness of our IoT attack
detection framework.
12 Oct 2021
Network library APIs have historically been developed with the emphasis on data movement, placement, and communication semantics. Many communication semantics are available across a large variety of network libraries, such as send-receive, data streaming, put/get/atomic, RPC, active messages, collective communication, etc. In this work we introduce new compute and data movement APIs that overcome the constraints of the single-program, multiple-data (SPMD) programming model by allowing users to send binary executable code between processing elements. Our proof-of-concept implementation of the API is based on the UCX communication framework and leverages the RDMA network for fast compute migration. We envision the API being used to dispatch user functions from a host CPU to a SmartNIC (DPU), computational storage drive (CSD), or remote servers. In addition, the API can be used by large-scale irregular applications (such as semantic graph analysis), composed of many coordinating tasks operating on a data set so big that it has to be stored on many physical devices. In such cases, it may be more efficient to dynamically choose where code runs as the applications progresses.
Deep convolutional neural network (CNN) inference requires significant amount
of memory and computation, which limits its deployment on embedded devices. To
alleviate these problems to some extent, prior research utilize low precision
fixed-point numbers to represent the CNN weights and activations. However, the
minimum required data precision of fixed-point weights varies across different
networks and also across different layers of the same network. In this work, we
propose using floating-point numbers for representing the weights and
fixed-point numbers for representing the activations. We show that using
floating-point representation for weights is more efficient than fixed-point
representation for the same bit-width and demonstrate it on popular large-scale
CNNs such as AlexNet, SqueezeNet, GoogLeNet and VGG-16. We also show that such
a representation scheme enables compact hardware multiply-and-accumulate (MAC)
unit design. Experimental results show that the proposed scheme reduces the
weight storage by up to 36% and power consumption of the hardware multiplier by
up to 50%.
Async-HFL introduces a framework for efficient and robust asynchronous federated learning in hierarchical IoT networks, combining multi-tier asynchronous aggregation with adaptive system management. The approach achieved up to 96.8x faster convergence than synchronous methods and 1.31x faster than state-of-the-art asynchronous baselines, alongside communication savings and demonstrated robustness in physical IoT deployments.
There are no more papers matching your filters at the moment.