BIFOLD
Large language model (LLM) developers aim for their models to be honest, helpful, and harmless. However, when faced with malicious requests, models are trained to refuse, sacrificing helpfulness. We show that frontier LLMs can develop a preference for dishonesty as a new strategy, even when other options are available. Affected models respond to harmful requests with outputs that sound harmful but are crafted to be subtly incorrect or otherwise harmless in practice. This behavior emerges with hard-to-predict variations even within models from the same model family. We find no apparent cause for the propensity to deceive, but show that more capable models are better at executing this strategy. Strategic dishonesty already has a practical impact on safety evaluations, as we show that dishonest responses fool all output-based monitors used to detect jailbreaks that we test, rendering benchmark scores unreliable. Further, strategic dishonesty can act like a honeypot against malicious users, which noticeably obfuscates prior jailbreak attacks. While output monitors fail, we show that linear probes on internal activations can be used to reliably detect strategic dishonesty. We validate probes on datasets with verifiable outcomes and by using them as steering vectors. Overall, we consider strategic dishonesty as a concrete example of a broader concern that alignment of LLMs is hard to control, especially when helpfulness and harmlessness conflict.
The hypothesis that Convolutional Neural Networks (CNNs) are inherently texture-biased has shaped much of the discourse on feature use in deep learning. We revisit this hypothesis by examining limitations in the cue-conflict experiment by Geirhos et al. To address these limitations, we propose a domain-agnostic framework that quantifies feature reliance through systematic suppression of shape, texture, and color cues, avoiding the confounds of forced-choice conflicts. By evaluating humans and neural networks under controlled suppression conditions, we find that CNNs are not inherently texture-biased but predominantly rely on local shape features. Nonetheless, this reliance can be substantially mitigated through modern training strategies or architectures (ConvNeXt, ViTs). We further extend the analysis across computer vision, medical imaging, and remote sensing, revealing that reliance patterns differ systematically: computer vision models prioritize shape, medical imaging models emphasize color, and remote sensing models exhibit a stronger reliance on texture. Code is available at this https URL.
Researchers from Technische Universität Berlin and BIFOLD developed PRISM, a framework to generate multi-concept textual descriptions for Large Language Model features, explicitly addressing polysemanticity. PRISM achieves superior description quality compared to prior methods and provides empirical evidence that individual LLM features encode diverse concepts, with its polysemanticity scores aligning with human judgments.
Large language models (LLMs) excel in many tasks of software engineering, yet progress in leveraging them for vulnerability discovery has stalled in recent years. To understand this phenomenon, we investigate LLMs through the lens of classic code metrics. Surprisingly, we find that a classifier trained solely on these metrics performs on par with state-of-the-art LLMs for vulnerability discovery. A root-cause analysis reveals a strong correlation and a causal effect between LLMs and code metrics: When the value of a metric is changed, LLM predictions tend to shift by a corresponding magnitude. This dependency suggests that LLMs operate at a similarly shallow level as code metrics, limiting their ability to grasp complex patterns and fully realize their potential in vulnerability discovery. Based on these findings, we derive recommendations on how research should more effectively address this challenge.
Anomaly detection plays a pivotal role in automated industrial inspection, aiming to identify subtle or rare defects in otherwise uniform visual patterns. As collecting representative examples of all possible anomalies is infeasible, we tackle structural anomaly detection using a self-supervised autoencoder that learns to repair corrupted inputs. To this end, we introduce a corruption model that injects artificial disruptions into training images to mimic structural defects. While reminiscent of denoising autoencoders, our approach differs in two key aspects. First, instead of unstructured i.i.d.\ noise, we apply structured, spatially coherent perturbations that make the task a hybrid of segmentation and inpainting. Second, and counterintuitively, we add and preserve Gaussian noise on top of the occlusions, which acts as a Tikhonov regularizer anchoring the Jacobian of the reconstruction function toward identity. This identity-anchored regularization stabilizes reconstruction and further improves both detection and segmentation accuracy. On the MVTec AD benchmark, our method achieves state-of-the-art results (I/P-AUROC: 99.9/99.4), supporting our theoretical framework and demonstrating its practical relevance for automatic inspection.
Researchers at BIFOLD & TU Berlin demonstrated that AI-based weather forecasting systems, such as GenCast-like models, are vulnerable to adversarial attacks. Manipulating as little as 0.1% of weather observations can induce or conceal extreme weather events like heat waves, intense rainfall, or hurricanes, and these perturbations often evade detection by standard quality control mechanisms.
18 Sep 2025
Modern recommender systems heavily leverage user interaction data to deliver personalized experiences. However, relying on personal data presents challenges in adhering to privacy regulations, such as the GDPR's "right to be forgotten". Machine unlearning (MU) aims to address these challenges by enabling the efficient removal of specific training data from models post-training, without compromising model utility or leaving residual information. However, current benchmarks for unlearning in recommender systems -- most notably CURE4Rec -- fail to reflect real-world operational demands. They focus narrowly on collaborative filtering, overlook tasks like session-based and next-basket recommendation, simulate unrealistically large unlearning requests, and ignore critical efficiency constraints. In this paper, we propose a set of design desiderata and research questions to guide the development of a more realistic benchmark for unlearning in recommender systems, with the goal of gathering feedback from the research community. Our benchmark proposal spans multiple recommendation tasks, includes domain-specific unlearning scenarios, and several unlearning algorithms -- including ones adapted from a recent NeurIPS unlearning competition. Furthermore, we argue for an unlearning setup that reflects the sequential, time-sensitive nature of real-world deletion requests. We also present a preliminary experiment in a next-basket recommendation setting based on our proposed desiderata and find that unlearning also works for sequential recommendation models, exposed to many small unlearning requests. In this case, we observe that a modification of a custom-designed unlearning algorithm for recommender systems outperforms general unlearning algorithms significantly, and that unlearning can be executed with a latency of only several seconds.
Deep learning has enabled remarkable progress in binary code analysis. In
particular, pre-trained embeddings of assembly code have become a gold standard
for solving analysis tasks, such as measuring code similarity or recognizing
functions. These embeddings are capable of learning a vector representation
from unlabeled code. In contrast to natural language processing, however, label
information is not scarce for many tasks in binary code analysis. For example,
labeled training data for function boundaries, optimization levels, and
argument types can be easily derived from debug information provided by a
compiler. Consequently, the main motivation of embeddings does not transfer
directly to binary code analysis.
In this paper, we explore the role of pre-trained embeddings from a critical
perspective. To this end, we systematically evaluate recent embeddings for
assembly code on five downstream tasks using a corpus of 1.2 million functions
from the Debian distribution. We observe that several embeddings perform
similarly when sufficient labeled data is available, and that differences
reported in prior work are hardly noticeable. Surprisingly, we find that
end-to-end learning without pre-training performs best on average, which calls
into question the need for specialized embeddings. By varying the amount of
labeled data, we eventually derive guidelines for when embeddings offer
advantages and when end-to-end learning is preferable for binary code analysis.
Self-supervised learning (SSL) has proven to be a powerful approach for
extracting biologically meaningful representations from single-cell data. To
advance our understanding of SSL methods applied to single-cell data, we
present scSSL-Bench, a comprehensive benchmark that evaluates nineteen SSL
methods. Our evaluation spans nine datasets and focuses on three common
downstream tasks: batch correction, cell type annotation, and missing modality
prediction. Furthermore, we systematically assess various data augmentation
strategies. Our analysis reveals task-specific trade-offs: the specialized
single-cell frameworks, scVI, CLAIRE, and the finetuned scGPT excel at
uni-modal batch correction, while generic SSL methods, such as VICReg and
SimCLR, demonstrate superior performance in cell typing and multi-modal data
integration. Random masking emerges as the most effective augmentation
technique across all tasks, surpassing domain-specific augmentations. Notably,
our results indicate the need for a specialized single-cell multi-modal data
integration framework. scSSL-Bench provides a standardized evaluation platform
and concrete recommendations for applying SSL to single-cell analysis,
advancing the convergence of deep learning and single-cell genomics.
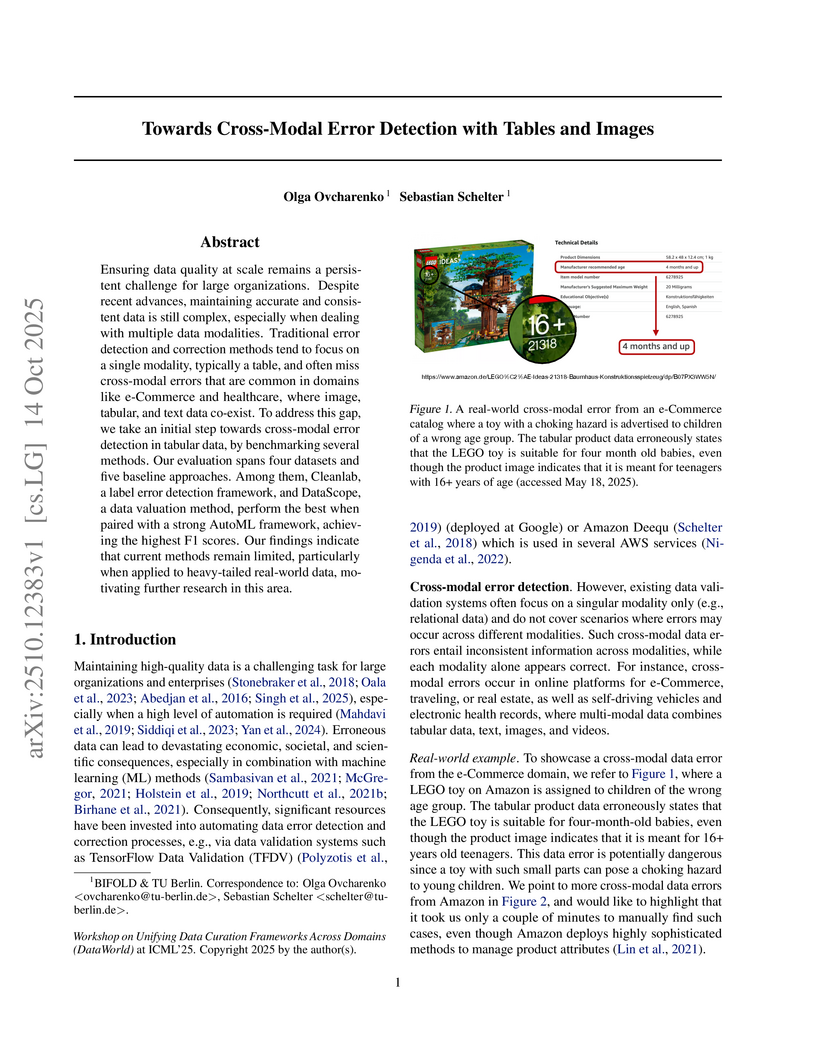
Ensuring data quality at scale remains a persistent challenge for large organizations. Despite recent advances, maintaining accurate and consistent data is still complex, especially when dealing with multiple data modalities. Traditional error detection and correction methods tend to focus on a single modality, typically a table, and often miss cross-modal errors that are common in domains like e-Commerce and healthcare, where image, tabular, and text data co-exist. To address this gap, we take an initial step towards cross-modal error detection in tabular data, by benchmarking several methods. Our evaluation spans four datasets and five baseline approaches. Among them, Cleanlab, a label error detection framework, and DataScope, a data valuation method, perform the best when paired with a strong AutoML framework, achieving the highest F1 scores. Our findings indicate that current methods remain limited, particularly when applied to heavy-tailed real-world data, motivating further research in this area.
Investigating critical phenomena or phase transitions is of high interest in
physics and chemistry, for which Monte Carlo (MC) simulations, a crucial tool
for numerically analyzing macroscopic properties of given systems, are often
hindered by an emerging divergence of correlation length -- known as scale
invariance at criticality (SIC) in the renormalization group theory. SIC causes
the system to behave the same at any length scale, from which many existing
sampling methods suffer: long-range correlations cause critical slowing down in
Markov chain Monte Carlo (MCMC), and require intractably large receptive fields
for generative samplers. In this paper, we propose a Renormalization-informed
Generative Critical Sampler (RiGCS) -- a novel sampler specialized for
near-critical systems, where SIC is leveraged as an advantage rather than a
nuisance. Specifically, RiGCS builds on MultiLevel Monte Carlo (MLMC) with Heat
Bath (HB) algorithms, which perform ancestral sampling from low-resolution to
high-resolution lattice configurations with site-wise-independent conditional
HB sampling. Although MLMC-HB is highly efficient under exact SIC, it suffers
from a low acceptance rate under slight SIC violation. Notably, SIC violation
always occurs in finite-size systems, and may induce long-range and
higher-order interactions in the renormalized distributions, which are not
considered by independent HB samplers. RiGCS enhances MLMC-HB by replacing a
part of the conditional HB sampler with generative models that capture those
residual interactions and improve the sampling efficiency. Our experiments show
that the effective sample size of RiGCS is a few orders of magnitude higher
than state-of-the-art generative model baselines in sampling configurations for
128x128 two-dimensional Ising systems.
A common paradigm for improving fuzzing performance is to focus on selected
regions of a program rather than its entirety. While previous work has largely
explored how these locations can be reached, their selection, that is, the
where, has received little attention so far. A common paradigm for improving
fuzzing performance is to focus on selected regions of a program rather than
its entirety. While previous work has largely explored how these locations can
be reached, their selection, that is, the where, has received little attention
so far. In this paper, we fill this gap and present the first comprehensive
analysis of target selection methods for fuzzing. To this end, we examine
papers from leading security and software engineering conferences, identifying
prevalent methods for choosing targets. By modeling these methods as general
scoring functions, we are able to compare and measure their efficacy on a
corpus of more than 1,600 crashes from the OSS-Fuzz project. Our analysis
provides new insights for target selection in practice: First, we find that
simple software metrics significantly outperform other methods, including
common heuristics used in directed fuzzing, such as recently modified code or
locations with sanitizer instrumentation. Next to this, we identify language
models as a promising choice for target selection. In summary, our work offers
a new perspective on directed fuzzing, emphasizing the role of target selection
as an orthogonal dimension to improve performance.
25 Aug 2025
Join ordering is a key factor in query performance, yet traditional cost-based optimizers often produce sub-optimal plans due to inaccurate cardinality estimates in multi-predicate, multi-join queries. Existing alternatives such as learning-based optimizers and adaptive query processing improve accuracy but can suffer from high training costs, poor generalization, or integration challenges. We present an extension of OmniSketch - a probabilistic data structure combining count-min sketches and K-minwise hashing - to enable multi-join cardinality estimation without assuming uniformity and independence. Our approach introduces the OmniSketch join estimator, ensures sketch interoperability across tables, and provides an algorithm to process alpha-acyclic join graphs. Our experiments on SSB-skew and JOB-light show that OmniSketch-enhanced cost-based optimization can improve estimation accuracy and plan quality compared to DuckDB. For SSB-skew, we show intermediate result decreases up to 1,077x and execution time decreases up to 3.19x. For JOB-light, OmniSketch join cardinality estimation shows occasional individual improvements but largely suffers from a loss of witnesses due to unfavorable join graph shapes and large numbers of unique values in foreign key columns.
Entity matching (EM) is the problem of determining whether two records refer to same real-world entity, which is crucial in data integration, e.g., for product catalogs or address databases. A major drawback of many EM approaches is their dependence on labelled examples. We thus focus on the challenging setting of zero-shot entity matching where no labelled examples are available for an unseen target dataset. Recently, large language models (LLMs) have shown promising results for zero-shot EM, but their low throughput and high deployment cost limit their applicability and scalability.
We revisit the zero-shot EM problem with AnyMatch, a small language model fine-tuned in a transfer learning setup. We propose several novel data selection techniques to generate fine-tuning data for our model, e.g., by selecting difficult pairs to match via an AutoML filter, by generating additional attribute-level examples, and by controlling label imbalance in the data.
We conduct an extensive evaluation of the prediction quality and deployment cost of our model, in a comparison to thirteen baselines on nine benchmark datasets. We find that AnyMatch provides competitive prediction quality despite its small parameter size: it achieves the second-highest F1 score overall, and outperforms several other approaches that employ models with hundreds of billions of parameters. Furthermore, our approach exhibits major cost benefits: the average prediction quality of AnyMatch is within 4.4% of the state-of-the-art method MatchGPT with the proprietary trillion-parameter model GPT-4, yet AnyMatch requires four orders of magnitude less parameters and incurs a 3,899 times lower inference cost (in dollars per 1,000 tokens).
This study comprehensively evaluates the table understanding capabilities of Large Language Models (LLMs) and Multimodal LLMs (MLLMs) across scientific and non-scientific domains and various table representation modalities. It introduces TableEval, a new benchmark dataset unifying diverse table formats, and finds that models struggle significantly with scientific tables while exhibiting robustness to different text-based table serializations.
14 Nov 2023
Sensor data streams occur widely in various real-time applications in the context of the Internet of Things (IoT). However, sensor data streams feature missing values due to factors such as sensor failures, communication errors, or depleted batteries. Missing values can compromise the quality of real-time analytics tasks and downstream applications. Existing imputation methods either make strong assumptions about streams or have low efficiency. In this study, we aim to accurately and efficiently impute missing values in data streams that satisfy only general characteristics in order to benefit real-time applications more widely. First, we propose a message propagation imputation network (MPIN) that is able to recover the missing values of data instances in a time window. We give a theoretical analysis of why MPIN is effective. Second, we present a continuous imputation framework that consists of data update and model update mechanisms to enable MPIN to perform continuous imputation both effectively and efficiently. Extensive experiments on multiple real datasets show that MPIN can outperform the existing data imputers by wide margins and that the continuous imputation framework is efficient and accurate.
The development of foundation models through pretraining of vision-language
models (VLMs) has recently attracted great attention in remote sensing (RS).
VLM pretraining aims to learn image and language alignments from a large number
of image-text pairs. Each pretraining image is often associated with multiple
captions containing redundant information due to repeated or semantically
similar phrases, resulting in increased pretraining and inference time. To
overcome this, we introduce a weighted feature aggregation (WFA) strategy for
VLM pretraining in RS. Our strategy aims to extract and exploit complementary
information from multiple captions per image while reducing redundancies
through feature aggregation with importance weighting. To calculate adaptive
importance weights for different captions of each image, we propose two
techniques: (i) non-parametric uniqueness and (ii) learning-based attention. In
the first technique, importance weights are calculated based on the bilingual
evaluation understudy (BLEU) scores of the captions to emphasize unique
sentences and reduce the influence of repetitive ones. In the second technique,
importance weights are learned through an attention mechanism instead of
relying on hand-crafted features. The effectiveness of the proposed WFA
strategy with the two techniques is analyzed in terms of downstream performance
on text-to-image retrieval in RS. Experimental results show that the proposed
strategy enables efficient and effective pretraining of VLMs in RS. Based on
the experimental analysis, we derive guidelines for selecting appropriate
techniques depending on downstream task requirements and resource constraints.
The code of this work is publicly available at
this https URL
Contrastive explanations, where one decision is explained in contrast to another, are supposed to be closer to how humans explain a decision than non-contrastive explanations, where the decision is not necessarily referenced to an alternative. This claim has never been empirically validated. We analyze four English text-classification datasets (SST2, DynaSent, BIOS and DBpedia-Animals). We fine-tune and extract explanations from three different models (RoBERTa, GTP-2, and T5), each in three different sizes and apply three post-hoc explainability methods (LRP, GradientxInput, GradNorm). We furthermore collect and release human rationale annotations for a subset of 100 samples from the BIOS dataset for contrastive and non-contrastive settings. A cross-comparison between model-based rationales and human annotations, both in contrastive and non-contrastive settings, yields a high agreement between the two settings for models as well as for humans. Moreover, model-based explanations computed in both settings align equally well with human rationales. Thus, we empirically find that humans do not necessarily explain in a contrastive manner.9 pages, long paper at ACL 2022 proceedings.
User-generated data sources have gained significance in uncovering Adverse
Drug Reactions (ADRs), with an increasing number of discussions occurring in
the digital world. However, the existing clinical corpora predominantly revolve
around scientific articles in English. This work presents a multilingual corpus
of texts concerning ADRs gathered from diverse sources, including patient fora,
social media, and clinical reports in German, French, and Japanese. Our corpus
contains annotations covering 12 entity types, four attribute types, and 13
relation types. It contributes to the development of real-world multilingual
language models for healthcare. We provide statistics to highlight certain
challenges associated with the corpus and conduct preliminary experiments
resulting in strong baselines for extracting entities and relations between
these entities, both within and across languages.
Techniques for knowledge graph (KGs) enrichment have been increasingly
crucial for commercial applications that rely on evolving product catalogues.
However, because of the huge search space of potential enrichment, predictions
from KG completion (KGC) methods suffer from low precision, making them
unreliable for real-world catalogues. Moreover, candidate facts for enrichment
have varied relevance to users. While making correct predictions for incomplete
triplets in KGs has been the main focus of KGC method, the relevance of when to
apply such predictions has been neglected. Motivated by the product search use
case, we address the angle of generating relevant completion for a catalogue
using user search behaviour and the users property association with a product.
In this paper, we present our intuition for identifying enrichable data points
and use general-purpose KGs to show-case the performance benefits. In
particular, we extract entity-predicate pairs from user queries, which are more
likely to be correct and relevant, and use these pairs to guide the prediction
of KGC methods. We assess our method on two popular encyclopedia KGs, DBPedia
and YAGO 4. Our results from both automatic and human evaluations show that
query guidance can significantly improve the correctness and relevance of
prediction.
There are no more papers matching your filters at the moment.