Meta Platforms
FlexAttention, developed by Meta Platforms and the University of Michigan-Ann Arbor, provides a compiler-driven programming model that bridges the performance-flexibility gap in attention mechanisms. It enables researchers to implement diverse attention variants using standard PyTorch code while achieving performance comparable to specialized kernels like FlashAttention, including a 5.49x-8.00x speedup over PyTorch SDPA for unsupported variants.
Researchers at Meta Platforms developed Reinforcement Learning with Performance Feedback (RLPF) to post-train large language models for generating online ad text. This approach, leveraging real-world click-through rate data as a reward signal, led to a 6.7% increase in advertiser-level CTR and an 18.5% increase in ad variations created during a large-scale A/B test on Facebook.
13 Nov 2025
While LLM-based agents are able to tackle a wide variety of code reasoning questions, the answers are not always correct. This prevents the agent from being useful in situations where high precision is desired: (1) helping a software engineer understand a new code base, (2) helping a software engineer during code review sessions, and (3) ensuring that the code generated by an automated code generation system meets certain requirements (e.g. fixes a bug, improves readability, implements a feature).
As a result of this lack of trustworthiness, the agent's answers need to be manually verified before they can be trusted. Manually confirming responses from a code reasoning agent requires human effort and can result in slower developer productivity, which weakens the assistance benefits of the agent. In this paper, we describe a method to automatically validate the answers provided by a code reasoning agent by verifying its reasoning steps. At a very high level, the method consists of extracting a formal representation of the agent's response and, subsequently, using formal verification and program analysis tools to verify the agent's reasoning steps.
We applied this approach to a benchmark set of 20 uninitialized variable errors detected by sanitizers and 20 program equivalence queries. For the uninitialized variable errors, the formal verification step was able to validate the agent's reasoning on 13/20 examples, and for the program equivalence queries, the formal verification step successfully caught 6/8 incorrect judgments made by the agent.
This paper describes Meta's ACH system for mutation-guided LLM-based test generation. ACH generates relatively few mutants (aka simulated faults), compared to traditional mutation testing. Instead, it focuses on generating currently undetected faults that are specific to an issue of concern. From these currently uncaught faults, ACH generates tests that can catch them, thereby `killing' the mutants and consequently hardening the platform against regressions. We use privacy concerns to illustrate our approach, but ACH can harden code against {\em any} type of regression. In total, ACH was applied to 10,795 Android Kotlin classes in 7 software platforms deployed by Meta, from which it generated 9,095 mutants and 571 privacy-hardening test cases. ACH also deploys an LLM-based equivalent mutant detection agent that achieves a precision of 0.79 and a recall of 0.47 (rising to 0.95 and 0.96 with simple pre-processing). ACH was used by Messenger and WhatsApp test-a-thons where engineers accepted 73% of its tests, judging 36% to privacy relevant. We conclude that ACH hardens code against specific concerns and that, even when its tests do not directly tackle the specific concern, engineers find them useful for their other benefits.
Large-scale recommendation systems are pivotal to process an immense volume of daily user interactions, requiring the effective modeling of high cardinality and heterogeneous features to ensure accurate predictions. In prior work, we introduced Hierarchical Sequential Transducers (HSTU), an attention-based architecture for modeling high cardinality, non-stationary streaming recommendation data, providing good scaling law in the generative recommender framework (GR). Recent studies and experiments demonstrate that attending to longer user history sequences yields significant metric improvements. However, scaling sequence length is activation-heavy, necessitating parallelism solutions to effectively shard activation memory. In transformer-based LLMs, context parallelism (CP) is a commonly used technique that distributes computation along the sequence-length dimension across multiple GPUs, effectively reducing memory usage from attention activations. In contrast, production ranking models typically utilize jagged input tensors to represent user interaction features, introducing unique CP implementation challenges. In this work, we introduce context parallelism with jagged tensor support for HSTU attention, establishing foundational capabilities for scaling up sequence dimensions. Our approach enables a 5.3x increase in supported user interaction sequence length, while achieving a 1.55x scaling factor when combined with Distributed Data Parallelism (DDP).
08 Apr 2025
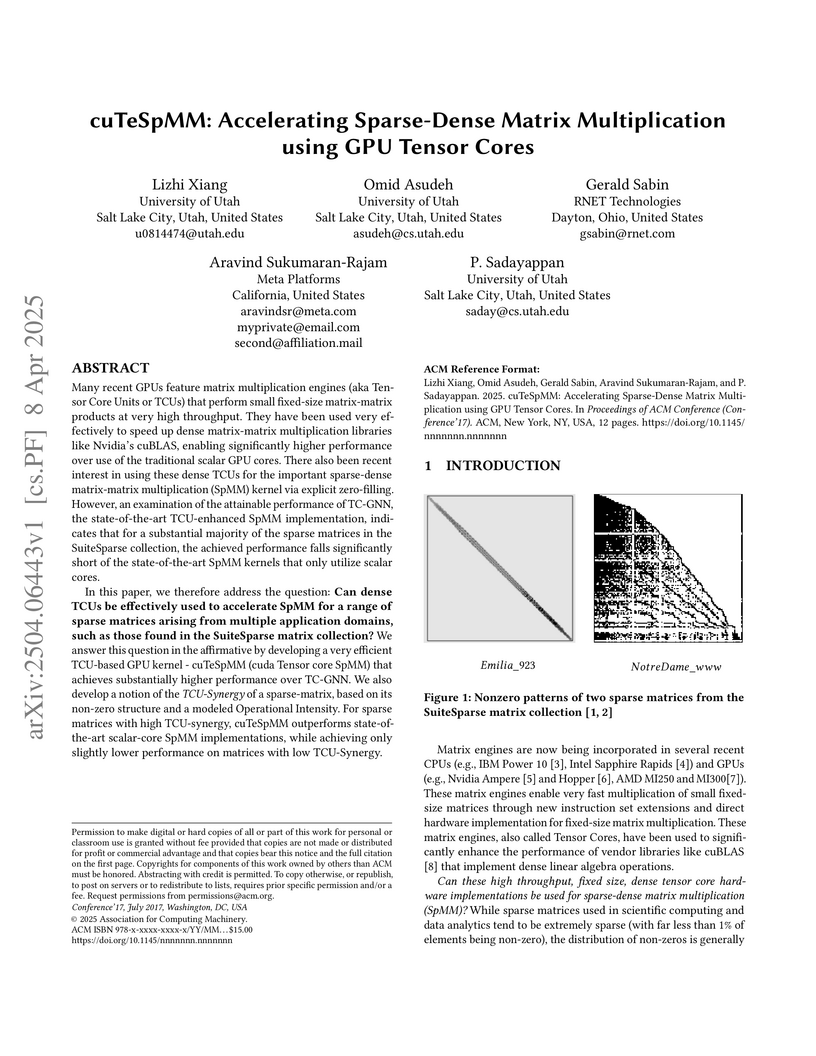
Many recent GPUs feature matrix multiplication engines (aka Tensor Core Units
or TCUs) that perform small fixed-size matrix-matrix products at very high
throughput. They have been used very effectively to speed up dense
matrix-matrix multiplication libraries like Nvidia's cuBLAS, enabling
significantly higher performance over use of the traditional scalar GPU cores.
There also been recent interest in using these dense TCUs for the important
sparse-dense matrix-matrix multiplication (SpMM) kernel via explicit
zero-filling.
However, an examination of the attainable performance of TC-GNN, the
state-of-the-art TCU-enhanced SpMM implementation, indicates that for a
substantial majority of the sparse matrices in the SuiteSparse collection, the
achieved performance falls significantly short of the state-of-the-art SpMM
kernels that only utilize scalar cores.
In this paper, we therefore address the question: Can dense TCUs be
effectively used to accelerate SpMM for a range of sparse matrices arising from
multiple application domains, such as those found in the SuiteSparse matrix
collection? We answer this question in the affirmative by developing a very
efficient TCU-based GPU kernel - cuTeSpMM (cuda Tensor core SpMM) that achieves
substantially higher performance over TC-GNN. We also develop a notion of the
TCU-Synergy of a sparse-matrix, based on its non-zero structure and a modeled
Operational Intensity. For sparse matrices with high TCU-synergy, cuTeSpMM
outperforms state-of-the-art scalar-core SpMM implementations, while achieving
only slightly lower performance on matrices with low TCU-Synergy.
In content moderation for social media platforms, the cost of delaying the
review of a content is proportional to its view trajectory, which fluctuates
and is apriori unknown. Motivated by such uncertain holding costs, we consider
a queueing model where job states evolve based on a Markov chain with
state-dependent instantaneous holding costs. We demonstrate that in the
presence of such uncertain holding costs, the two canonical algorithmic
principles, instantaneous-cost (cμ-rule) and expected-remaining-cost
(cμ/θ-rule), are suboptimal. By viewing each job as a Markovian
ski-rental problem, we develop a new index-based algorithm,
Opportunity-adjusted Remaining Cost (OaRC), that adjusts to the opportunity of
serving jobs in the future when uncertainty partly resolves. We show that the
regret of OaRC scales as O~(L1.5N), where L is the maximum
length of a job's holding cost trajectory and N is the system size. This
regret bound shows that OaRC achieves asymptotic optimality when the system
size N scales to infinity. Moreover, its regret is independent of the
state-space size, which is a desirable property when job states contain
contextual information. We corroborate our results with an extensive simulation
study based on two holding cost patterns (online ads and user-generated
content) that arise in content moderation for social media platforms. Our
simulations based on synthetic and real datasets demonstrate that OaRC
consistently outperforms existing practice, which is based on the two canonical
algorithmic principles.
As privacy-centric changes reshape the digital advertising landscape, deterministic attribution and measurement of advertising-related user behavior is increasingly constrained. In response, there has been a resurgence in the use of traditional probabilistic measurement techniques, such as media and marketing mix modeling (m/MMM), particularly among digital-first advertisers. However, small and midsize businesses often lack the resources to implement advanced proprietary modeling systems, which require specialized expertise and significant team investments. To address this gap, marketing data scientists at Meta have developed the open-source computational package Robyn, designed to facilitate the adoption of m/MMM for digital advertising measurement. This article explores the computational components and design choices that underpin Robyn, emphasizing how it "packages up" m/MMM to promote organizational acceptance and mitigate common biases. As a widely adopted and actively maintained open-source tool, Robyn is continually evolving. Consequently, the solutions described here should not be seen as definitive or conclusive but as an outline of the pathways that the Robyn community has embarked on. This article aims to provide a structured introduction to these evolving practices, encouraging feedback and dialogue to ensure that Robyn's development aligns with the needs of the broader data science community.
The deployment of Large Language Models (LLMs) in recommender systems for predicting Click-Through Rates (CTR) necessitates a delicate balance between computational efficiency and predictive accuracy. This paper presents an optimization framework that combines Retrieval-Augmented Generation (RAG) with an innovative multi-head early exit architecture to concurrently enhance both aspects. By integrating Graph Convolutional Networks (GCNs) as efficient retrieval mechanisms, we are able to significantly reduce data retrieval times while maintaining high model performance. The early exit strategy employed allows for dynamic termination of model inference, utilizing real-time predictive confidence assessments across multiple heads. This not only quickens the responsiveness of LLMs but also upholds or improves their accuracy, making it ideal for real-time application scenarios. Our experiments demonstrate how this architecture effectively decreases computation time without sacrificing the accuracy needed for reliable recommendation delivery, establishing a new standard for efficient, real-time LLM deployment in commercial systems.
Although eye-tracking technology is being integrated into more VR and MR headsets, the true potential of eye tracking in enhancing user interactions within XR settings remains relatively untapped. Presently, one of the most prevalent gaze applications in XR is input control; for example, using gaze to control a cursor for pointing. However, our eyes evolved primarily for sensory input and understanding of the world around us, and yet few XR applications have leveraged natural gaze behavior to infer and support users' intent and cognitive states. Systems that can represent a user's context and interaction intent can better support the user by generating contextually relevant content, by making the user interface easier to use, by highlighting potential errors, and more. This mode of application is not fully taken advantage of in current commercially available XR systems and yet it is likely where we'll find paradigm-shifting use cases for eye tracking. In this paper, we elucidate the state-of-the-art applications for eye tracking and propose new research directions to harness its potential fully.
Building multisensory AI systems that learn from multiple sensory inputs such as text, speech, video, real-world sensors, wearable devices, and medical data holds great promise for impact in many scientific areas with practical benefits, such as in supporting human health and well-being, enabling multimedia content processing, and enhancing real-world autonomous agents. By synthesizing a range of theoretical frameworks and application domains, this thesis aims to advance the machine learning foundations of multisensory AI. In the first part, we present a theoretical framework formalizing how modalities interact with each other to give rise to new information for a task. These interactions are the basic building blocks in all multimodal problems, and their quantification enables users to understand their multimodal datasets, design principled approaches to learn these interactions, and analyze whether their model has succeeded in learning. In the second part, we study the design of practical multimodal foundation models that generalize over many modalities and tasks, which presents a step toward grounding large language models to real-world sensory modalities. We introduce MultiBench, a unified large-scale benchmark across a wide range of modalities, tasks, and research areas, followed by the cross-modal attention and multimodal transformer architectures that now underpin many of today's multimodal foundation models. Scaling these architectures on MultiBench enables the creation of general-purpose multisensory AI systems, and we discuss our collaborative efforts in applying these models for real-world impact in affective computing, mental health, cancer prognosis, and robotics. Finally, we conclude this thesis by discussing how future work can leverage these ideas toward more general, interactive, and safe multisensory AI.
One of the key challenges in federated learning (FL) is local data
distribution heterogeneity across clients, which may cause inconsistent feature
spaces across clients. To address this issue, we propose a novel method FedFM,
which guides each client's features to match shared category-wise anchors
(landmarks in feature space). This method attempts to mitigate the negative
effects of data heterogeneity in FL by aligning each client's feature space.
Besides, we tackle the challenge of varying objective function and provide
convergence guarantee for FedFM. In FedFM, to mitigate the phenomenon of
overlapping feature spaces across categories and enhance the effectiveness of
feature matching, we further propose a more precise and effective feature
matching loss called contrastive-guiding (CG), which guides each local feature
to match with the corresponding anchor while keeping away from
non-corresponding anchors. Additionally, to achieve higher efficiency and
flexibility, we propose a FedFM variant, called FedFM-Lite, where clients
communicate with server with fewer synchronization times and communication
bandwidth costs. Through extensive experiments, we demonstrate that FedFM with
CG outperforms several works by quantitative and qualitative comparisons.
FedFM-Lite can achieve better performance than state-of-the-art methods with
five to ten times less communication costs.
Despite decades of research and practice in automated software testing,
several fundamental concepts remain ill-defined and under-explored, yet offer
enormous potential real-world impact. We show that these concepts raise
exciting new challenges in the context of Large Language Models for software
test generation. More specifically, we formally define and investigate the
properties of hardening and catching tests. A hardening test is one that seeks
to protect against future regressions, while a catching test is one that
catches such a regression or a fault in new functionality introduced by a code
change. Hardening tests can be generated at any time and may become catching
tests when a future regression is caught. We also define and motivate the
Catching 'Just-in-Time' (JiTTest) Challenge, in which tests are generated
'just-in-time' to catch new faults before they land into production. We show
that any solution to Catching JiTTest generation can also be repurposed to
catch latent faults in legacy code. We enumerate possible outcomes for
hardening and catching tests and JiTTests, and discuss open research problems,
deployment options, and initial results from our work on automated LLM-based
hardening at Meta. This paper was written to accompany the keynote by the
authors at the ACM International Conference on the Foundations of Software
Engineering (FSE) 2025. Author order is alphabetical. The corresponding author
is Mark Harman.
Deep learning models like Convolutional Neural Networks and transformers have shown impressive capabilities in speech verification, gaining considerable attention in the research community. However, CNN-based approaches struggle with modeling long-sequence audio effectively, resulting in suboptimal verification performance. On the other hand, transformer-based methods are often hindered by high computational demands, limiting their practicality. This paper presents the MASV model, a novel architecture that integrates the Mamba module into the ECAPA-TDNN framework. By introducing the Local Context Bidirectional Mamba and Tri-Mamba block, the model effectively captures both global and local context within audio sequences. Experimental results demonstrate that the MASV model substantially enhances verification performance, surpassing existing models in both accuracy and efficiency.
Asynchronously replicated primary-backup databases are commonly deployed to improve availability and offload read-only transactions. To both apply replicated writes from the primary and serve read-only transactions, the backups implement a cloned concurrency control protocol. The protocol ensures read-only transactions always return a snapshot of state that previously existed on the primary. This compels the backup to exactly copy the commit order resulting from the primary's concurrency control. Existing cloned concurrency control protocols guarantee this by limiting the backup's parallelism. As a result, the primary's concurrency control executes some workloads with more parallelism than these protocols. In this paper, we prove that this parallelism gap leads to unbounded replication lag, where writes can take arbitrarily long to replicate to the backup and which has led to catastrophic failures in production systems. We then design C5, the first cloned concurrency protocol to provide bounded replication lag. We implement two versions of C5: Our evaluation in MyRocks, a widely deployed database, demonstrates C5 provides bounded replication lag. Our evaluation in Cicada, a recent in-memory database, demonstrates C5 keeps up with even the fastest of primaries.
The integration of hardware accelerators has significantly advanced the capabilities of modern recommendation systems, enabling the exploration of complex ranking paradigms previously deemed impractical. However, the GPU-based computational costs present substantial challenges. In this paper, we demonstrate our development of an efficiency-driven approach to explore these paradigms, moving beyond traditional reliance on native PyTorch modules. We address the specific challenges posed by ranking models' dependence on categorical features, which vary in length and complicate GPU utilization. We introduce Jagged Feature Interaction Kernels, a novel method designed to extract fine-grained insights from long categorical features through efficient handling of dynamically sized tensors. We further enhance the performance of attention mechanisms by integrating Jagged tensors with Flash Attention. Our novel Jagged Flash Attention achieves up to 9x speedup and 22x memory reduction compared to dense attention. Notably, it also outperforms dense flash attention, with up to 3x speedup and 53% more memory efficiency. In production models, we observe 10% QPS improvement and 18% memory savings, enabling us to scale our recommendation systems with longer features and more complex architectures.
We introduce and study the k-center clustering problem with set outliers, a natural and practical generalization of the classical k-center clustering with outliers. Instead of removing individual data points, our model allows discarding up to z subsets from a given family of candidate outlier sets H. Given a metric space (P,dist), where P is a set of elements and dist a distance metric, a family of sets H⊆2P, and parameters k,z, the goal is to compute a set of k centers S⊆P and a family of z sets H⊆H to minimize maxp∈P∖(⋃h∈Hh)mins∈Sdist(p,s). This abstraction captures structured noise common in database applications, such as faulty data sources or corrupted records in data integration and sensor systems.
We present the first approximation algorithms for this problem in both general and geometric settings. Our methods provide tri-criteria approximations: selecting up to 2k centers and 2fz outlier sets (where f is the maximum number of sets that a point belongs to), while achieving O(1)-approximation in clustering cost. In geometric settings, we leverage range and BBD trees to achieve near-linear time algorithms. In many real applications f=1. In this case we further improve the running time of our algorithms by constructing small \emph{coresets}. We also provide a hardness result for the general problem showing that it is unlikely to get any sublinear approximation on the clustering cost selecting less than f⋅z outlier sets.
We demonstrate that this model naturally captures relational clustering with outliers: outliers are input tuples whose removal affects the join output. We provide approximation algorithms for both, establishing a tight connection between robust clustering and relational query evaluation.
We introduce FocalPose++, a neural render-and-compare method for jointly
estimating the camera-object 6D pose and camera focal length given a single RGB
input image depicting a known object. The contributions of this work are
threefold. First, we derive a focal length update rule that extends an existing
state-of-the-art render-and-compare 6D pose estimator to address the joint
estimation task. Second, we investigate several different loss functions for
jointly estimating the object pose and focal length. We find that a combination
of direct focal length regression with a reprojection loss disentangling the
contribution of translation, rotation, and focal length leads to improved
results. Third, we explore the effect of different synthetic training data on
the performance of our method. Specifically, we investigate different
distributions used for sampling object's 6D pose and camera's focal length when
rendering the synthetic images, and show that parametric distribution fitted on
real training data works the best. We show results on three challenging
benchmark datasets that depict known 3D models in uncontrolled settings. We
demonstrate that our focal length and 6D pose estimates have lower error than
the existing state-of-the-art methods.
19 Sep 2024
Tomographic volumetric additive manufacturing is a rapidly growing fabrication technology that enables rapid production of 3D objects through a single build step. In this process, the design of projections directly impacts geometric resolution, material properties, and manufacturing yield of the final printed part. Herein, we identify the hidden equivalent operations of three major existing projection optimization schemes and reformulate them into a general loss function where the optimization behavior can be systematically studied, and unique capabilities of the individual schemes can coalesce. The loss function formulation proposed in this study unified the optimization for binary and greyscale targets and generalized problem relaxation strategies with local tolerancing and weighting. Additionally, this formulation offers control on error sparsity and consistent dose response mapping throughout initialization, optimization, and evaluation. A parameter-sweep analysis in this study guides users in tuning optimization parameters for application-specific goals.
Due to its distributed nature, federated learning is vulnerable to poisoning
attacks, in which malicious clients poison the training process via
manipulating their local training data and/or local model updates sent to the
cloud server, such that the poisoned global model misclassifies many
indiscriminate test inputs or attacker-chosen ones. Existing defenses mainly
leverage Byzantine-robust federated learning methods or detect malicious
clients. However, these defenses do not have provable security guarantees
against poisoning attacks and may be vulnerable to more advanced attacks. In
this work, we aim to bridge the gap by proposing FLCert, an ensemble federated
learning framework, that is provably secure against poisoning attacks with a
bounded number of malicious clients. Our key idea is to divide the clients into
groups, learn a global model for each group of clients using any existing
federated learning method, and take a majority vote among the global models to
classify a test input. Specifically, we consider two methods to group the
clients and propose two variants of FLCert correspondingly, i.e., FLCert-P that
randomly samples clients in each group, and FLCert-D that divides clients to
disjoint groups deterministically. Our extensive experiments on multiple
datasets show that the label predicted by our FLCert for a test input is
provably unaffected by a bounded number of malicious clients, no matter what
poisoning attacks they use.
There are no more papers matching your filters at the moment.